By Rodrigo Montoro and Tempest’ researchers team
AWS Identity and Access Management (IAM) is a service where you can control access to various AWS resources by using the product to establish authentication and authorization rules.
Within this IAM universe, there are over 12,000 cataloged actions linked to the hundreds of services offered by AWS. Associated with these actions are access policies that are usually tied to the resources that can be accessed and their conditions. In other words, for a user to access a particular resource, it is necessary to have rules that specify the conditions under which this access can be done. These rules result from determining what action is possible for that user to do on that resource.
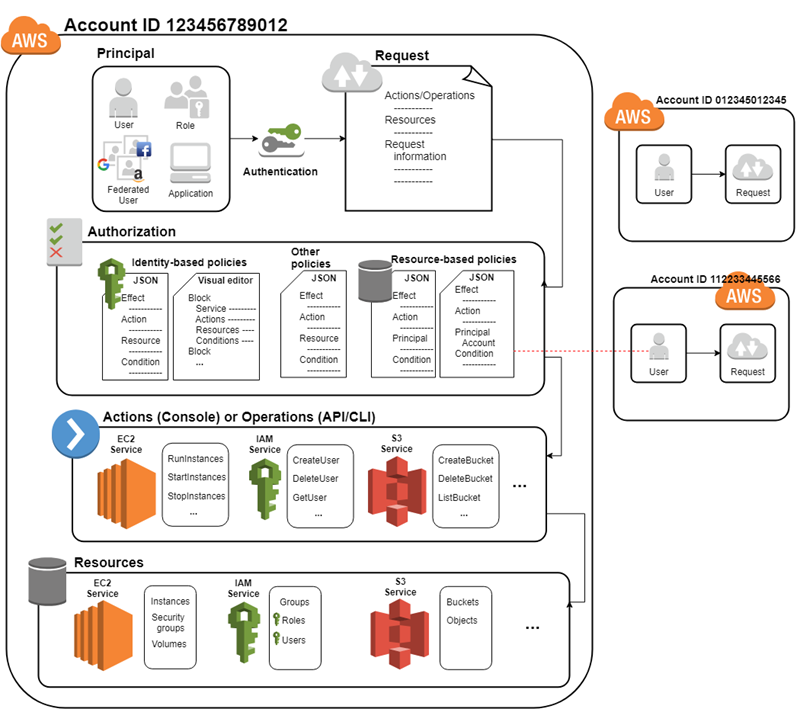
The basic flow of authentication and authorization (image below) works as follows:
1-) The “Principal”, which can be a user, a role, or an application, authenticates to the AWS control plane either directly or via IdP, Cross Account, and SSO.
2-) After authentication, the Principal’s permission is verified, and this permission originates from the policies associated with it, which can be a session, resource, or identity-based, among others.
3-) Once the permissions and their conditions are validated, the Principal will be able to perform the actions allowed on the resources assigned to him. Usually, this setting can be marked with an “*”, i.e., all.
Now that we understand how the control to access a resource in AWS works, we get to the real challenge, which is the use of policies in AWS based on the concept of minimum privilege. It’s very common in integrations with partners, such as SaaS services and consulting firms, to create a trusting relationship between the environments based on an access key, often using the AWS Managed Policy option known as ReadOnlyAccess. The tests here are related to version 86 (v86) of the policy, which can be found at this link.
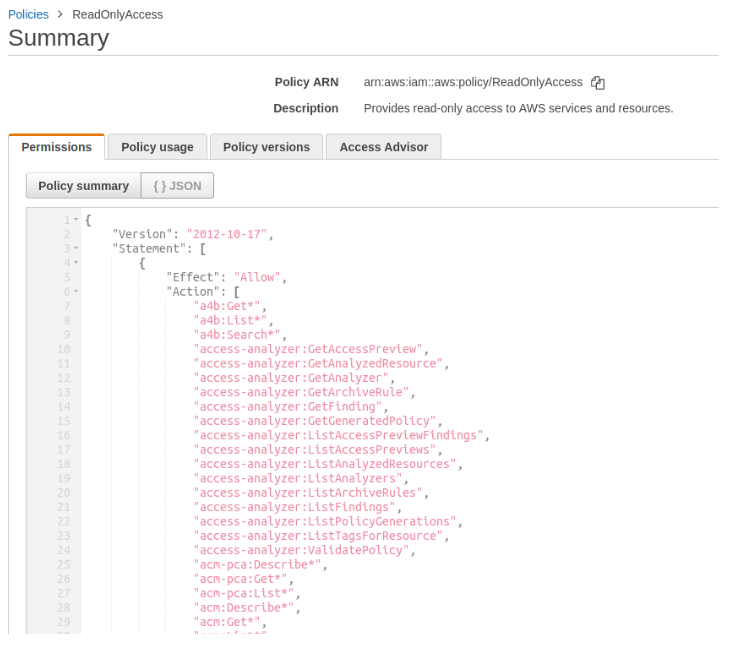
Based on this way of controlling access to services and how these interactions between third parties happen, we decided to dig deeper into the study of this policy, pointing out that the problems we report in this article are not in the ReadOnlyAccess policy itself but in the misunderstanding that administrators usually make out of it, using it like someone who copies and pastes a content without analyzing in detail the actions for which access is being granted and their possible impacts. Using ReadOnlyAccess in this way can have security impacts, especially if a person with bad intentions has access to a Principal with these privileges.
Using our favorite tool, adopted in several of our presentations and research, Cloudsplaining, we have identified thirteen (13) actions that are found and mapped into some category that can cause harm or risk to the company that adopts the policy without proper access review.
- cognito-identity:GetCredentialsForIdentity – Grants permission to return credentials for the provided identity ID.
- cognito-identity:GetOpenIdToken – Grants permission to get an OpenID token, using a known Cognito ID.
- cognito-identity:GetOpenIdTokenForDeveloperIdentity – Grants permission to register (or retrieve) a Cognito IdentityId and an OpenID Connect token for a user authenticated by your backend authentication process.
- cognito-idp:GetSigningCertificate – Returns the signing certificate.
- connect:GetFederationToken – Grants permission to federate into an Amazon Connect instance when using SAML-based authentication for identity management.
- ec2:GetPasswordData – Grants permission to retrieve the encrypted administrator password for a running Windows instance.
- ecr:GetAuthorizationToken – Grants permission to retrieve a token that is valid for a specified registry for 12 hours.
- gamelift:GetInstanceAccess – Grants permission to request remote access to a specified fleet instance.
- s3:GetObject – Grants permission to retrieve objects from Amazon S3.
- ssm:GetParameter – Grants permission to view information about a specified parameter.
- ssm:GetParameters – Grants permission to view information about multiple specified parameters.
- ssm:GetParametersByPath – Grants permission to view information about parameters in a specified hierarchy.
- sts:GetSessionToken – Grants permission to obtain a set of temporary security credentials (consisting of an access key ID, a secret access key, and a security token) for an AWS account or IAM user.
Thinking about the possibility that we may identify more risky actions in addition to the 13 above, we have deepened the investigation and mapped another 28 actions that can be misused in the course of an attack.
- apigateway:GET – Grants permission to read a particular resource.
- athena:GetDatabase – Grants permission to get a database for a given datacatalog. (athena:Get*)
- athena:GetQueryExecution – Grants permission to get information about the specified query execution. (athena:Get*)
- athena:GetQueryResults – Grants permission to get the query results. (athena:Get*)
- cassandra:Select – Grants permission to SELECT data from a table.
- chime:Retrieve* – Grants permission to download the file containing links to all user attachments returned as part of the “Request attachments” action.
- cloudtrail:LookupEvents – Grants permission to look up API activity events captured by CloudTrail that create, update, or delete resources in your account.
- codeartifact:GetAuthorizationToken – Grants permission to generate a temporary authentication token for accessing repositories in a domain.
- config:SelectResourceConfig – Grants permission to accept a structured query language (SQL) SELECT command, performs the corresponding search, and returns resource configurations matching the properties.
- datapipeline:QueryObjects – Grants permission to query the specified pipeline for the names of objects that match the specified set of conditions.
- dax:Query – Grants permission to use the primary key of a table or a secondary index to directly access items from that table or index.
- dax:Scan – Grants permission to return one or more items and item attributes by accessing every item in a table or a secondary index.
- dynamodb:GetRecords Grants permission to retrieve the stream records from a given shard. (dynamodb:Get*)
- dynamodb:Query – Grants permission to use the primary key of a table or a secondary index to directly access items from that table or index.
- dynamodb:Scan – Grants permission to return one or more items and item attributes by accessing every item in a table or a secondary index.
- ec2:DescribeInstanceAttribute – Grants permission to describe the attributes of an instance (userdata information). (ec2:Describe*)
- ec2:GetConsoleOutput – Grants permission to get the console output for an instance.
- ec2:GetConsoleScreenshot – Grants permission to retrieve a JPG-format screenshot of a running instance.
- es:ESHttpGet – Grants permission to send HTTP GET requests to the OpenSearch APIs.
- glue:GetDatabase – Grants permission to retrieve a database.
- glue:GetDatabases – Grants permission to retrieve all databases.
- glue:GetTable – Grants permission to retrieve a table.
- glue:GetTables – Grants permission to retrieve the tables in a database
- kendra:Query – Grants permission to query documents and faqs.
- lambda:GetFunction – Grants permission to view details about an AWS Lambda function. (lambda:Get*)
- logs:StartQuery – Grants permissions to schedule a query of a log group using CloudWatch Logs Insights.
- s3-object-lambda:GetObject – Grants permission to retrieve objects from Amazon S3.
- ssm:GetDocument Grants permission to view the contents of a specified SSM document. (ssm:Get*)
The information description was taken from https://aws.permissions.cloud/iam/
With this initial analysis, Tempest researchers identified at least 41 actions that can lead to improper data access, particularly when this policy is used to control the access of people from outside the organization. This list of twenty-eight (28) new actions can be added to the Cloudsplaining (after submitting, analyzing, and approving the responsible parties) so that those responsible for the environment will always be alerted when they are active because they are not only found in the ReadOnlyAccess policy.
We reiterate that the problem does not lie in the ReadOnlyAccess policy but in the lack of comprehension of access and authorization levels, as well as the consequent threats it provides, especially when we are talking about access to third parties, a situation in which the policy in question is commonly used.
Finally, whenever using a ready-made policy (AWS Managed Policy) like ReadOnlyAccess or creating something custom, try to be extra careful about the actions you include in the policies. Having as a best practice, the granting of minimal privilege is mandatory in this new cloud world. IAM is a super complex but critically important service for a successful security posture in environments like this.
Complete list of actions (41):
- apigateway:GET – Grants permission to read a particular resource.
- athena:GetDatabase – Grants permission to get a database for a given datacatalog. (athena:Get*)
- athena:GetQueryExecution – Grants permission to get information about the specified query execution. (athena:Get*)
- athena:GetQueryResults – Grants permission to get the query results. (athena:Get*)
- cassandra:Select – Grants permission to SELECT data from a table.
- chime:Retrieve* – Grants permission to download the file containing links to all user attachments returned as part of the “Request attachments” action.
- cloudtrail:LookupEvents – Grants permission to look up API activity events captured by CloudTrail that create, update, or delete resources in your account.
- codeartifact:GetAuthorizationToken – Grants permission to generate a temporary authentication token for accessing repositories in a domain.
- cognito-identity:GetCredentialsForIdentity – Grants permission to return credentials for the provided identity ID
- cognito-identity:GetOpenIdToken – Grants permission to get an OpenID token, using a known Cognito ID.
- cognito-identity:GetOpenIdTokenForDeveloperIdentity – Grants permission to register (or retrieve) a Cognito IdentityId and an OpenID Connect token for a user authenticated by your backend authentication process
- cognito-idp:GetSigningCertificate – Returns the signing certificate.
- config:SelectResourceConfig – Grants permission to accept a structured query language (SQL) SELECT command, performs the corresponding search, and returns resource configurations matching the properties. *
- connect:GetFederationToken – Grants permission to federate into an Amazon Connect instance when using SAML-based authentication for identity management.
- datapipeline:QueryObjects – Grants permission to query the specified pipeline for the names of objects that match the specified set of conditions.
- dax:Query – Grants permission to use the primary key of a table or a secondary index to directly access items from that table or index.
- dax:Scan – Grants permission to return one or more items and item attributes by accessing every item in a table or a secondary index.
- dynamodb:Get* – dynamodb:GetRecords Grants permission to retrieve the stream records from a given shard.
- dynamodb:Query – Grants permission to use the primary key of a table or a secondary index to directly access items from that table or index.
- dynamodb:Scan – Grants permission to return one or more items and item attributes by accessing every item in a table or a secondary index.
- ec2:DescribeInstanceAttribute – Grants permission to describe the attributes of an instance (userdata). (ec2:Describe*)
- ec2:GetConsoleOutput – Grants permission to get the console output for an instance.
- ec2:GetConsoleScreenshot – Grants permission to retrieve a JPG-format screenshot of a running instance.
- ec2:GetPasswordData – Grants permission to retrieve the encrypted administrator password for a running Windows instance.
- ecr:GetAuthorizationToken – Grants permission to retrieve a token that is valid for a specified registry for 12 hours.
- es:ESHttpGet – Grants permission to send HTTP GET requests to the OpenSearch APIs.
- gamelift:GetInstanceAccess – Grants permission to request remote access to a specified fleet instance.
- glue:GetDatabase – Grants permission to retrieve a database.
- glue:GetDatabases – Grants permission to retrieve all databases.
- glue:GetTable – Grants permission to retrieve a table.
- glue:GetTables – Grants permission to retrieve the tables in a database
- kendra:Query – Grants permission to query documents and faqs.
- lambda:GetFunction – Grants permission to view details about an AWS Lambda function. (lambda:Get*)
- logs:StartQuery – Grants permissions to schedule a query of a log group using CloudWatch Logs Insights.
- s3:GetObject – Grants permission to retrieve objects from Amazon S3.
- s3-object-lambda:GetObject – Grants permission to retrieve objects from Amazon S3.
- ssm:GetDocument Grants permission to view the contents of a specified SSM document. (ssm:Get*)
- ssm:GetParameter – Grants permission to view information about a specified parameter.
- ssm:GetParameters – Grants permission to view information about multiple specified parameters.
- ssm:GetParametersByPath – Grants permission to view information about parameters in a specified hierarchy.
- sts:GetSessionToken – Grants permission to obtain a set of temporary security credentials (consisting of an access key ID, a secret access key, and a security token) for an AWS account or IAM user.
Referências:
AWS User Guide. Understanding how IAM works. available at https://docs.aws.amazon.com/IAM/latest/UserGuide/intro-structure.html, accessed on 21 April 2022
AWS User Guide. What is IAM? available at https://docs.aws.amazon.com/IAM/latest/UserGuide/introduction.html, accessed on 21 April 2022
GRENU, Victor (Z0ph). MAMIP Bot. available at https://github.com/z0ph/MAMIP/blob/master/policies/ReadOnlyAccess, accessed on 21 April 2022
HOTNOPS. AWS ReadOnlyAccess: Not Even Once. available at https://posts.specterops.io/aws-readonlyaccess-not-even-once-ffbceb9fc908, accessed on 10 March 2022
SALESFORCE. Cloudsplaining GitHub. available at https://github.com/salesforce/cloudsplaining, accessed on 5 May 2022.
