Por Carlos Cabral
It is a common behavior among cybercriminals to take advantage of the fact that a subject is in evidence to use it as a motto to conduct various attacks, and since the crisis with the new coronavirus began, the subject has been used in several scams. We have already identified cyberthreats such as malicious apps, fake stores and websites, WhatsApp chains, updated versions of extortion scams, and even espionage using COVID-19 as a theme.
In this article we will focus on some of these strategies that, although frequently used by cybercriminals, may seem new to many people. We will also point out some recommendations for combating these threats.
Phishing
Phishing is the name given to a variety of techniques used in several scams. The word refers to fishing for victims. Several strategies discussed here may use at least one phishing technique, but roughly speaking this means sending messages to persuade the victim to do something such as click on a link, open a file, or install a computer virus.
Among the messages linked to COVID-19, the fact that a large company will donate alcohol gel to hospitals was exploited, for example, to extrapolate the news by saying that this donation would also cover individuals and asking victims to register on a fake website. They also took advantage of the fact that the Brazilian government is considering issuing R$ 200.00 vouchers to people in the most fragile situation to create a fake web page collecting information from the victims. Another case seeks to draw people’s attention to a video of the construction of a Chinese hospital for the treatment of the disease, but when the user clicks on the video, a computer virus is downloaded.
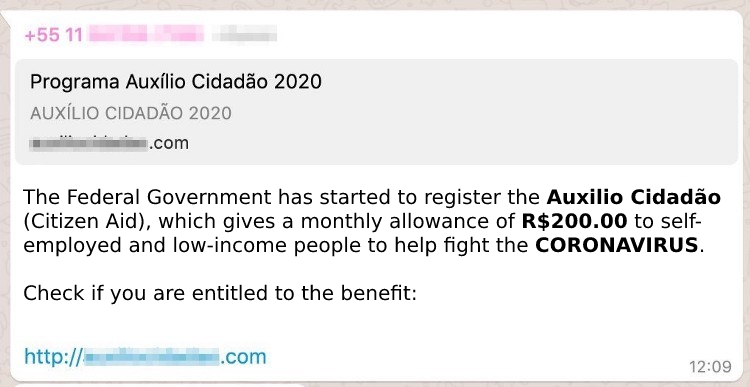
Above we cited three examples among the various scams that abuse this crisis, and it is important to say that scammers commonly use the most varied channels for the distribution of messages, such as e-mail, messaging apps, SMSs, and even phone calls.
However, although the “packaging” of the attack varies, behind it are components known to collect personal data from the victims, which are used in various forms of fraud, such as opening accounts, financing, buying goods, or making money from online advertisements. There are also computer viruses that collect personal data, but do more than that: they steal credit and debit card data and passwords. Some of them take advantage of the moment the victim accesses Internet Banking to pay bills, make loans or transfers with their account.
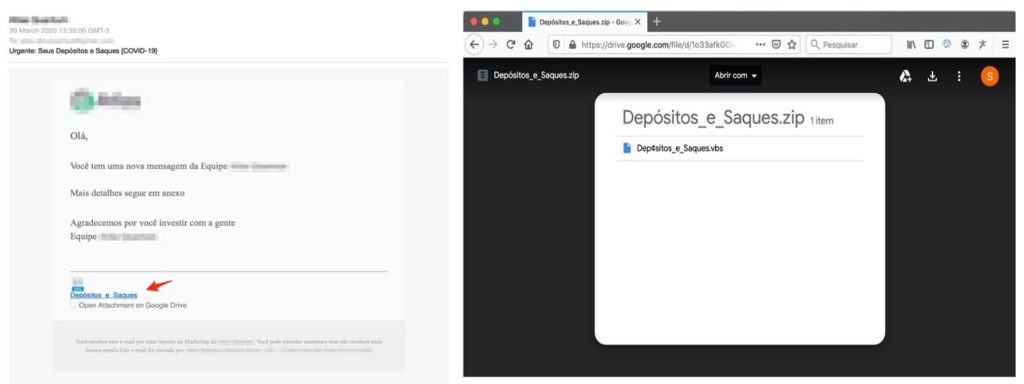
Fake store
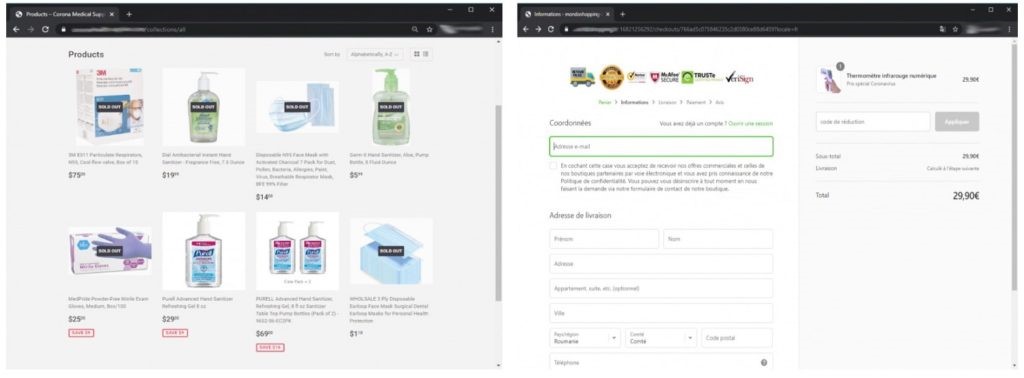
Although it is morally controversial, many people take advantage of situations like these to raise the prices of highly sought-after items such as alcohol gels and masks. Considering that such items are hard to find or are very expensive, fraudsters have created fake online stores that offer these products. It is even possible to find stores like these that charge via cryptocurrencies such as Bitcoin but never deliver the product, and others whose main purpose is to steal victims’ card details.
Sextortion Adapted
Sextortion is an extortion scam in which the criminal sends a message to the victim saying that he has compromised the victim’s computer and that he has found evidence that the victim has morally questionable behavior when using the Internet, thus demanding a payment, usually in Bitcoin, in order not to disclose the information he has.
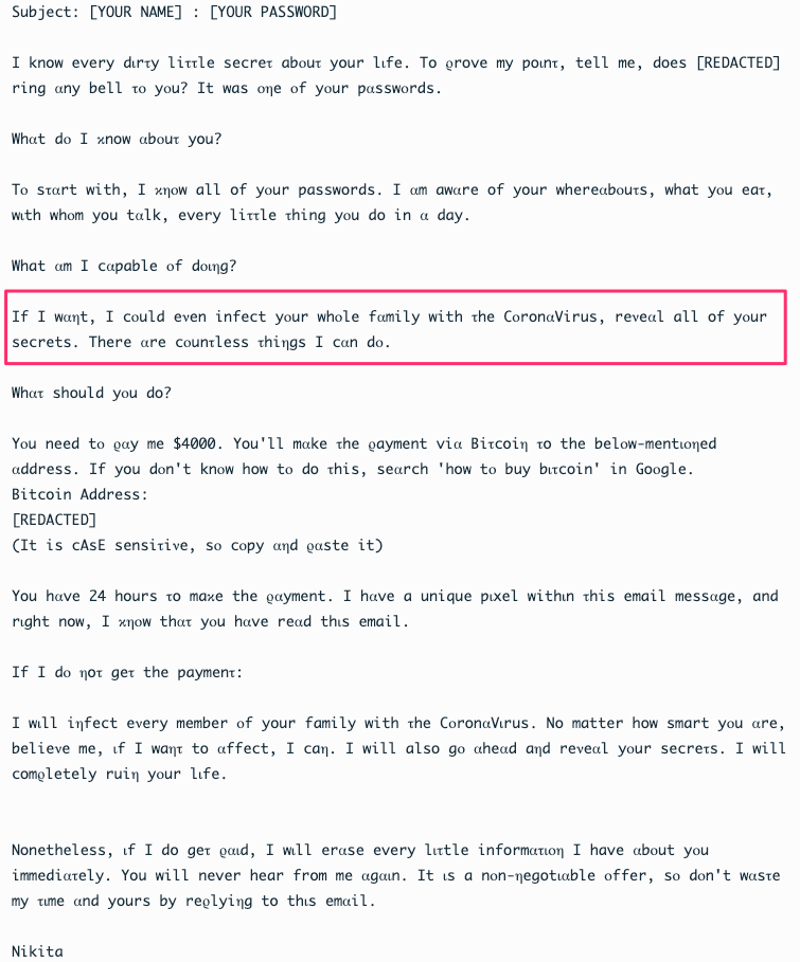
There are Sextortion messages saying that the criminal has obtained compromising photos from the computer, stored on the hard drive or taken directly from the webcam, and others claiming that the author has evidence that the victim accesses pornography. There are also cases where the perpetrator says he knows the victim’s secrets and says nothing more. To supposedly prove that he has the data he claims to have, the attacker shows the victim’s password in the message.
Attacks in which webcam images or computer data such as browsing history are obtained are possible. However, the overwhelming majority of the time the scam is a bluff in which the criminal has nothing but the victim’s password, which has been leaked in attacks that happen daily against the most varied services on the Internet.
He relies here on the fact that the victim recognizes the password and gets desperate about it, considering that people are comfortable using their computers, that everyone has their secrets, and that it is common to use the same password on several sites. So the victim ends up believing the message and falls for the scam.
This week an adapted version of sextortion for the new coronavirus crisis appeared, but the criminal says that besides divulging the victim’s information, he will infect his family with COVID-19. Pure bluff.
Ransomware
Following in the line of extortion scams, the Ransomware-based attack modality has become more and more frequent in recent years. It consists of a software program that encrypts the data on the victim’s computer or mobile device and demands a ransom, usually in Bitcoin, to deliver the key that decrypts the files.
Some recent versions of this threat also collect data from the computer before applying the encryption, also threatening the victim with information leakage.
One of the most talked-about ransomware attacks among experts in recent days is one that attempts to persuade victims to download an Android app that would supposedly track cases of infection by the new coronavirus near the user’s location.
Once the user downloads the app, it displays a message saying that the device is locked, requesting a reward payment.
Espionage
For years, countries have been spying on each other and also surveilling companies that somehow represent a strategic position aligned to each government’s interests. While there may be specific components behind each attack, the way of reaching the targets does not differ much from the techniques used by cybercrime, and of course the new coronavirus is being used as a theme in attacks for this purpose.
One of the attacks with this subject that has been prominent recently uses the new coronavirus as the subject in messages sent to specific targets, which contain an Excel spreadsheet manipulated in such a way as to install a computer virus. As soon as the user opens the spreadsheet and activates the macros, his computer is infected and the attackers can take control of the operating system.
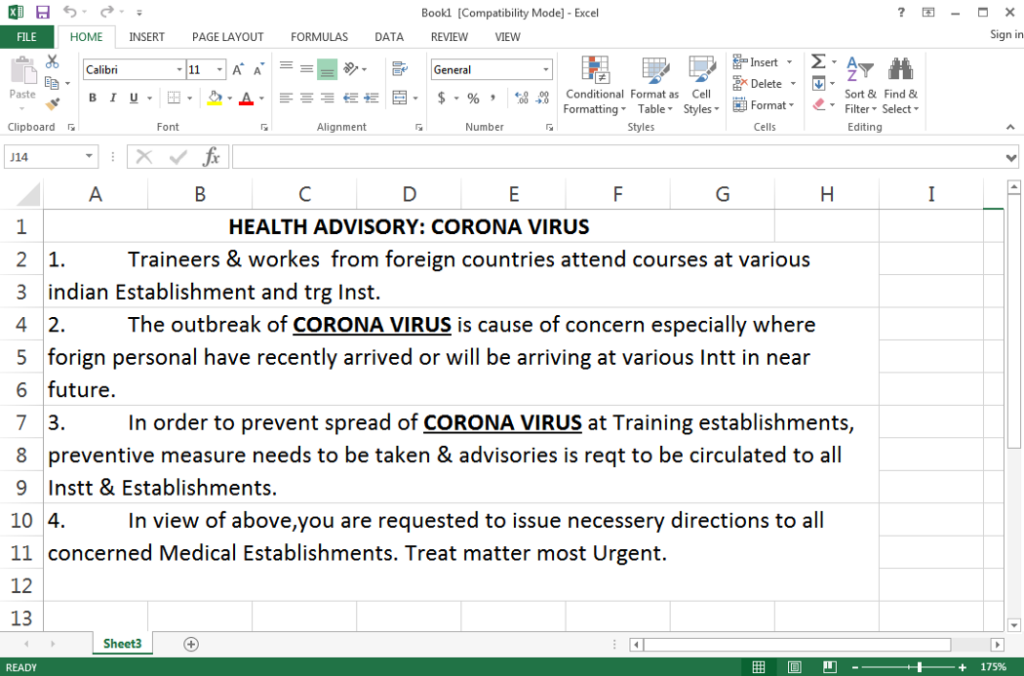
Theft
Recently, a scam was identified in which criminals pretended to be employees of telecommunications and cable TV companies doing maintenance services. They would ask to enter the victim’s home and then announce the robbery.
With the crisis of the new coronavirus, the scam has gained a new component, the announcement of a phone number falsely attributed to a hospital which appears in searches on the Internet for tests to detect the virus.
The victim contacts the criminals, gives his personal data and schedules a visit. The criminals arrive at the scheduled time disguised as healthcare professionals and announce the robbery as soon as they walk through the door.
How to face the problem
It is common for people to think that buying a security software product will solve everything. Products can help in some cases, but the most effective measure to avoid falling for these scams is free: the lesson that “if something is too good to be true, it probably isn’t true”.
If it is public knowledge that there is no alcohol gel on the market, and you see this product being sold very cheaply on an unknown website, be suspicious. If the news repeatedly says that there are few tests for the coronavirus in Brazil, that health professionals are all dedicated to treating patients, and you come across an announcement that a famous hospital will do the test in your home, be suspicious.
The logic to be applied is the same used to validate fake news. Check if the information is present in other sources, such as the press; access the official websites of the companies and look for information that confirms what is in the message that reached you before clicking on links, opening files attached to messages or calling suspicious services.
We are humans and no one can say that we will never succumb to a scam, especially when we are dealing with the fear of getting sick. But I bet if you have at least one story where you were saved by intuition, you will know that being suspicious of what you see on the Internet needs to be a general rule.
