By Threat Intelligence Team
-
Introduction
An important point for the monetization of financial scams applied by fraudsters is where to receive the funds transferred by the victims, whether they are people trying to purchase a product or service, or people who are being extorted by kidnapping, currently known as ‘Love Scam’ or ‘Pix (Brazilian Instant Payment System) Kidnapping’. In this scenario, the use of digital current accounts of “stooges”(Image 1), as they usually refer to accounts opened in the name of third parties, is introduced.
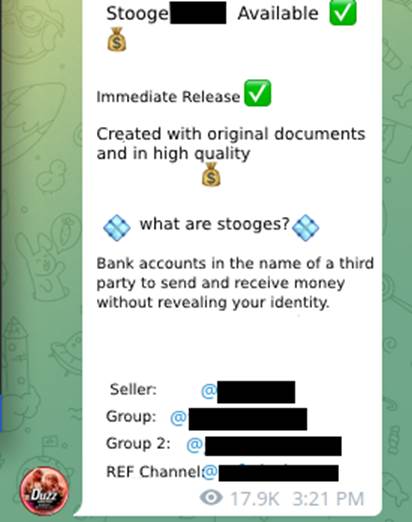
-
The stooge volunteer
2.1 Overview
What are volunteer stooges? They are individuals who knowingly pass on their digital checking account data to criminals to use for receiving money from illegal activities (Image 2).
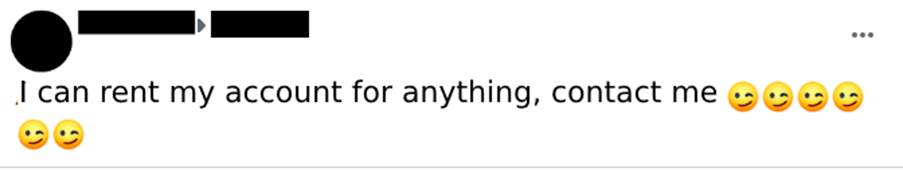
Although they have consented to give their bank details to obtain some advantage, many times, they do not know the real nature of the money that will be deposited in their accounts, which may be money from fraudulent transactions or even related to drug trafficking. The agreement between the parties, in general, is that a smaller percentage of the amount will remain with the holder of the account used to receive the money.
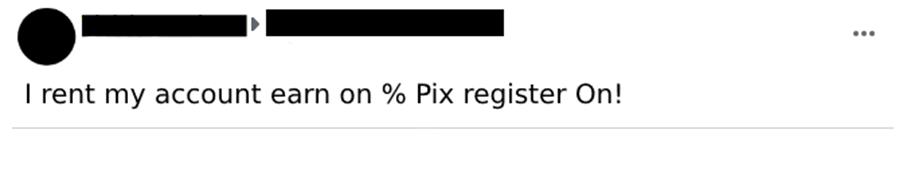
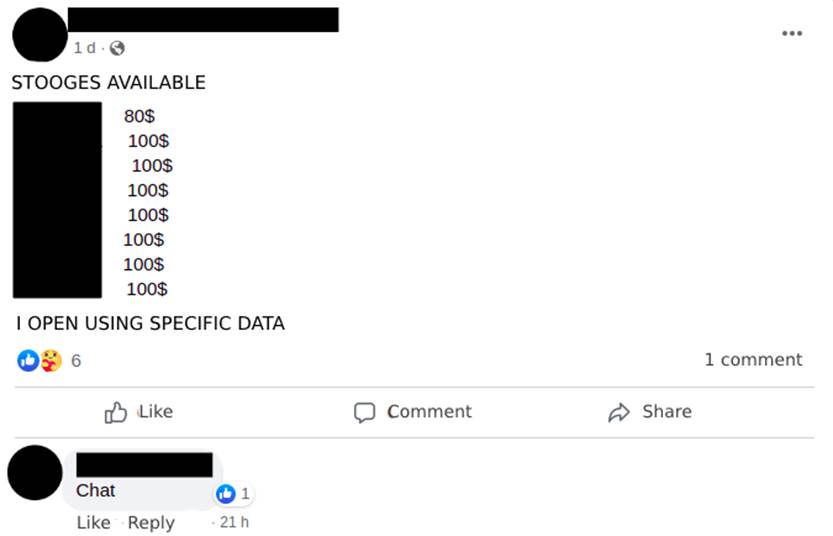
There are groups in social networks where the offer to “rent” these accounts is openly advertised and negotiated (Image 3).
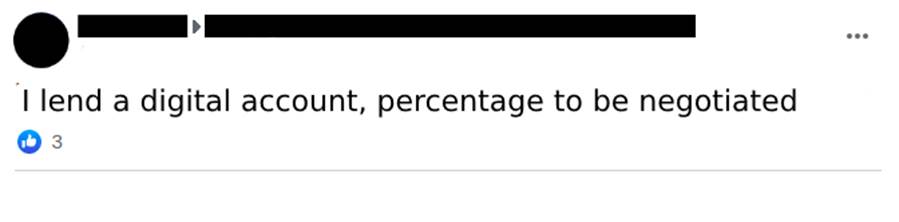
2.2 Prices
There is no pre-established value for renting digital checking accounts. It’s common to see a percentage negotiation. We have seen ads from people looking to lend the account with a fee of 45% of the deposited amount (Image 4), while those offering their accounts do not make clear the percentage of their fee (Image 5). We believe that this negotiation can reach an average of a 50-50 split between the fraudster and the account owner.
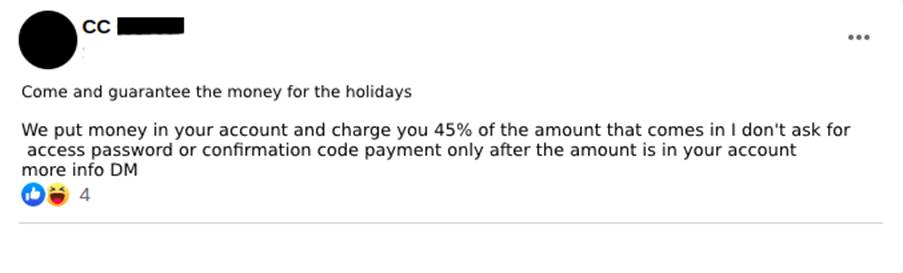
2.3 Supply and demand for renting accounts for transactions
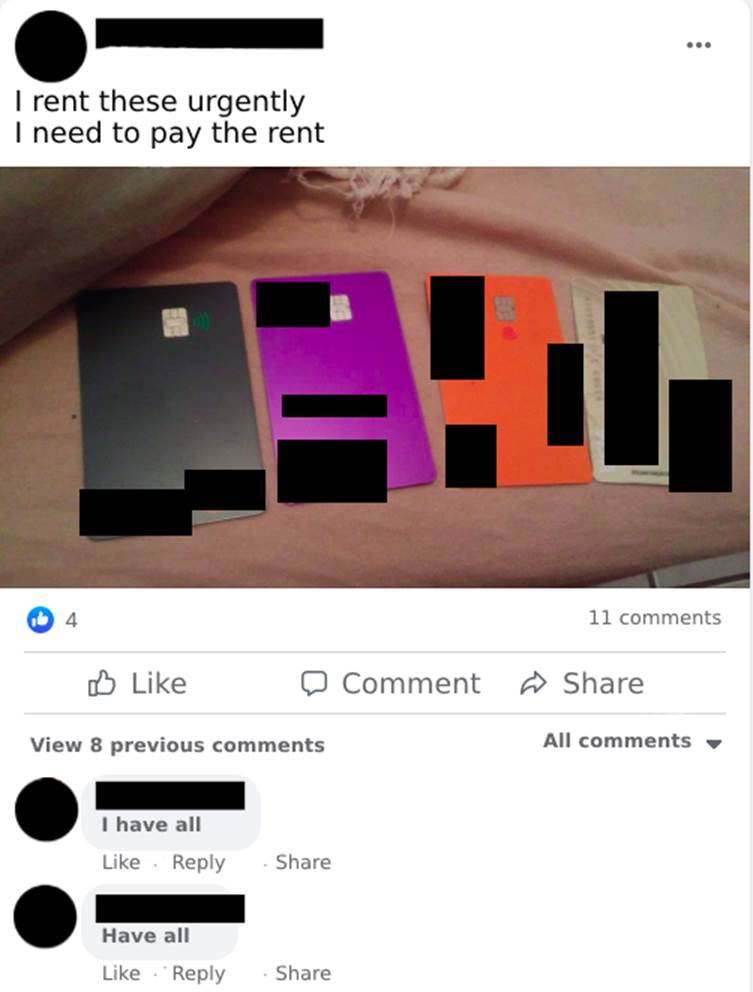
Financial problems may be the motivators for offering personal digital checking accounts for use in unknown acts. However, claiming ignorance of the purpose doesn’t exempt one from responsibility. It’s quite common to find people offering their accounts for rent on the social network Facebook (Meta). There are cases in which the renter even shows the cards, all in his name, of the accounts he has for rent, appealing to the fact that he needs to pay his outstanding bills (Image 6).
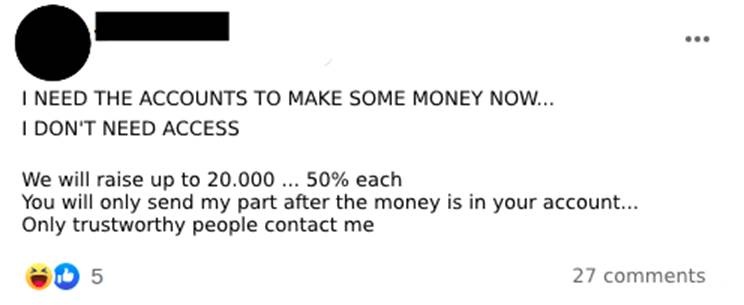
Slightly less common than people wanting to rent their accounts are criminals looking for individuals who agree to participate in scams by lending the account to receive some earnings from what is deposited in it. The advertisers don’t make it clear where the money comes from (Image 7).
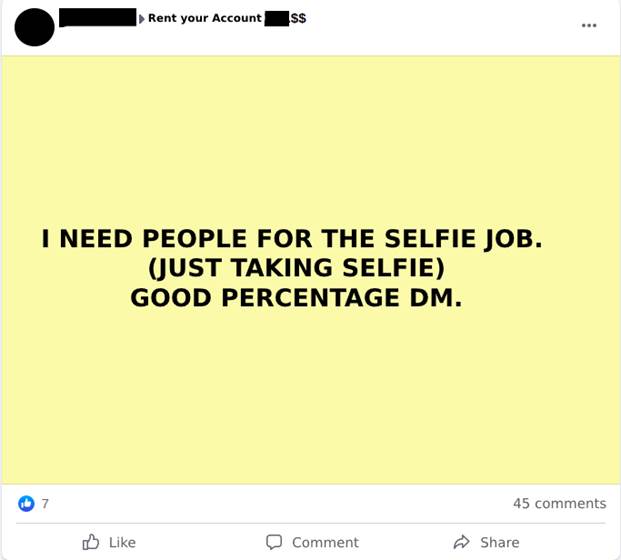
2.4 Search for volunteers to lend their faces (use of third party data)
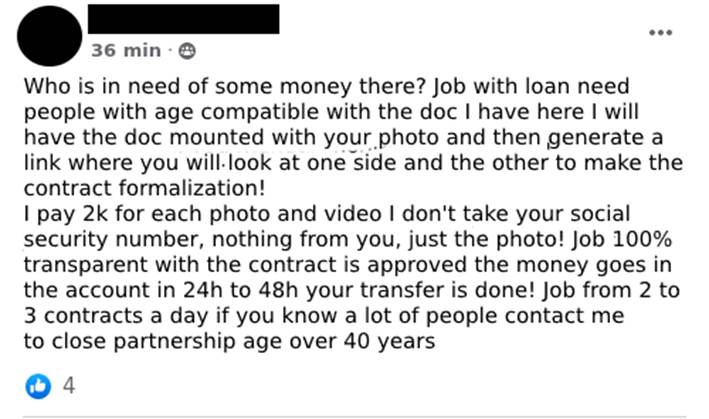
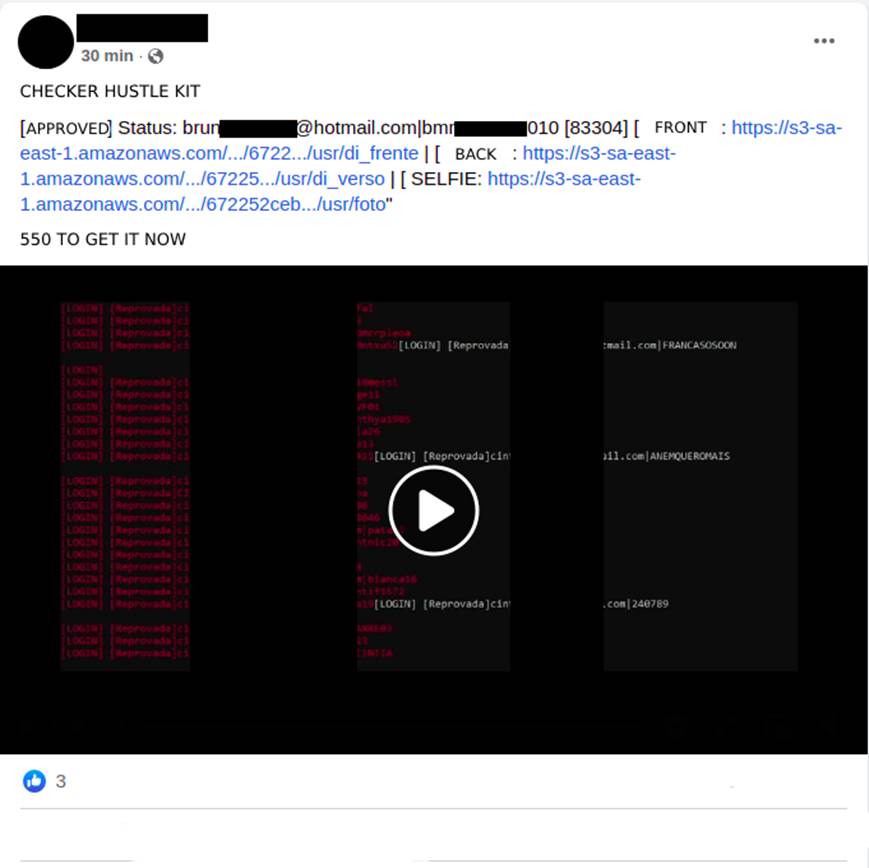
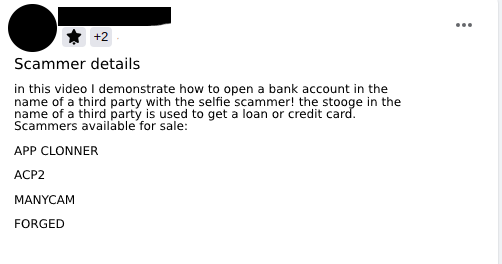
Another modality of volunteer is what can be called “stooge face”, in which the fraudster co-opts people who will have their faces used to validate the opening of digital checking accounts (Image 8). Using fake documents, created using the photograph of the co-opted person, the fraudster opens the account and generates a link for the stooge to validate the proof of life and image confirmation in order to open the account. With the account now open, the fraudster requests loans and, after receiving the amounts, promises to pay R$2,000.00 (two thousand Brazilian reals) for each loan contract approved (Image 9).
-
The Involuntary Stooge
3.1 Overview
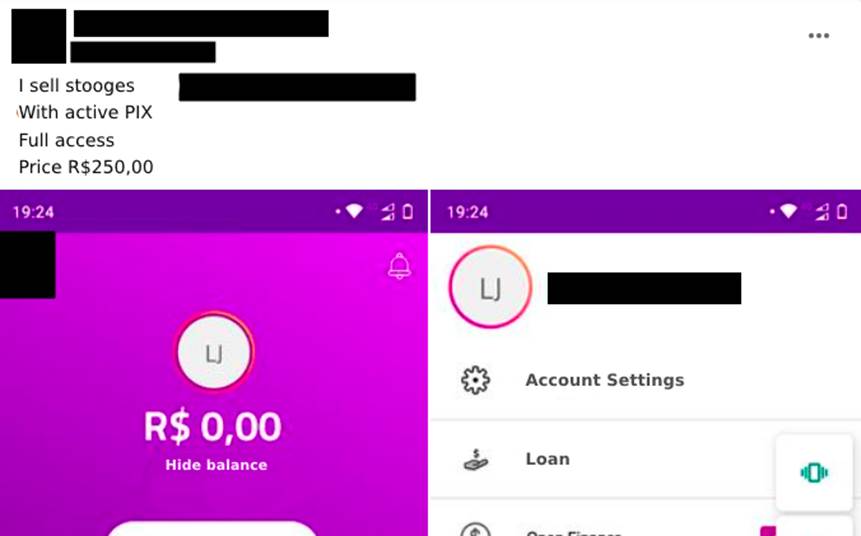
A very busy business is that of selling “stooge accounts” (Image 10). More experienced and persistent cybercriminals find ways to open digital checking accounts with others’ data without the third party being aware of the misuse of their personal information.
3.2 Prices
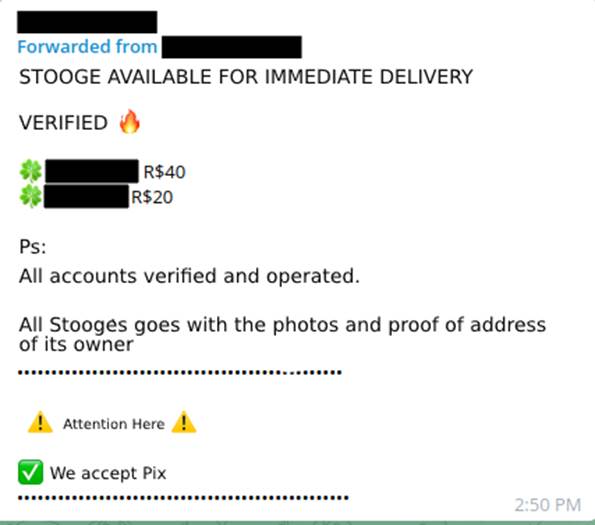
Since this is a well-publicized business, the values of the accounts vary from seller to seller, because many take into account the personal references of good salesmen they have within the groups and channels where the transactions take place. The initial amount advertised for a digital account is a modest R$20.00 (Image 11), while the highest value seen in the ads was R$250.00 (Image 12).
3.3 Theft and misuse of third-party documents
One of the ways used by fraudsters when opening accounts is the misuse of third parties’ personal data, including pictures of documents and pictures of people holding their documents close to their faces, known in the media as “Hustle Kit” (Image 13).
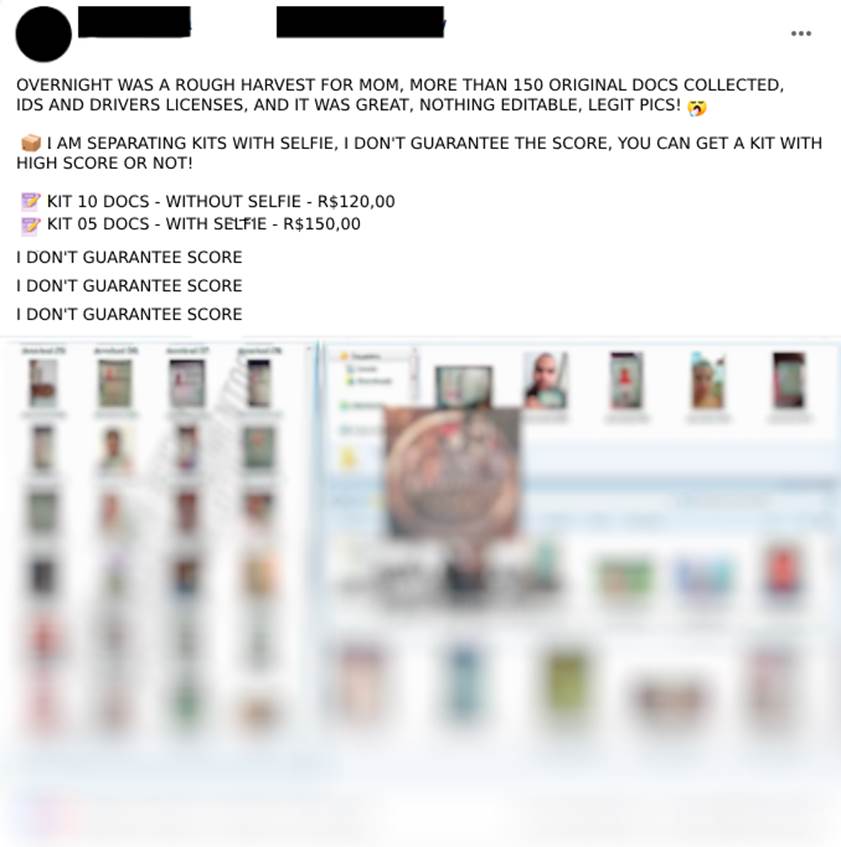
These documents are obtained in a variety of ways. One of the best known methods is social engineering scams, in which the attacker asks for photos and complete data when offering, for example, a false job opening, or can also be obtained through improper access to databases exposed on the Internet (Image 14).
In possession of this data and photos they are looking for banks that have fewer security mechanisms implemented in onboarding new customers.
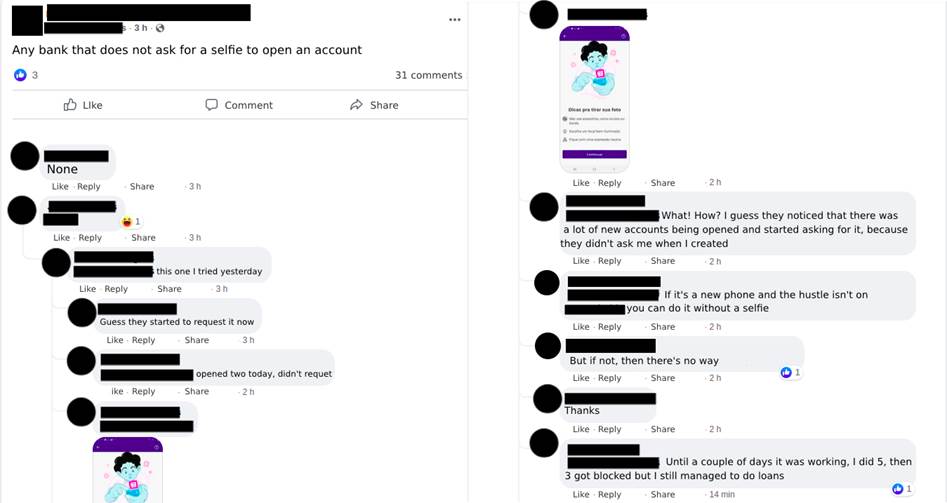
3.4 Interest in banks with less security factors
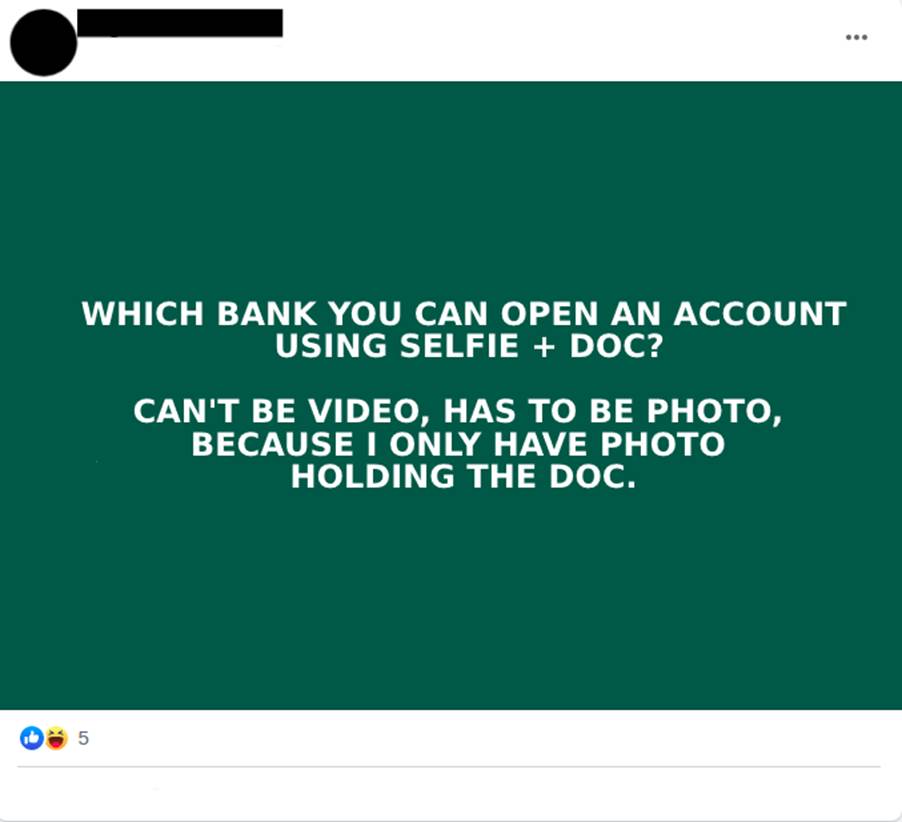
Although this is not a rule, smaller digital banks may have a low security maturity for the protection of their online business. With this, one of their main difficulties may be the process of evaluating the proof of life and ownership of the digital account opening applicant. Fraudsters often seek information about which banks would be most susceptible to failure in the process of setting up the digital account (Images 15 and 16). It’s also common to see conversations between cybercriminals in which onboarding facilities of certain digital banks are discussed (Image 17). They also sell scams in which they teach which banks and which techniques should be used for each target.

3.5 Creating accounts using a specific social security number
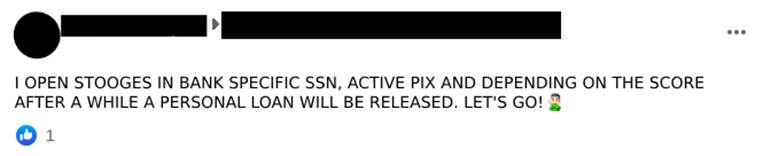
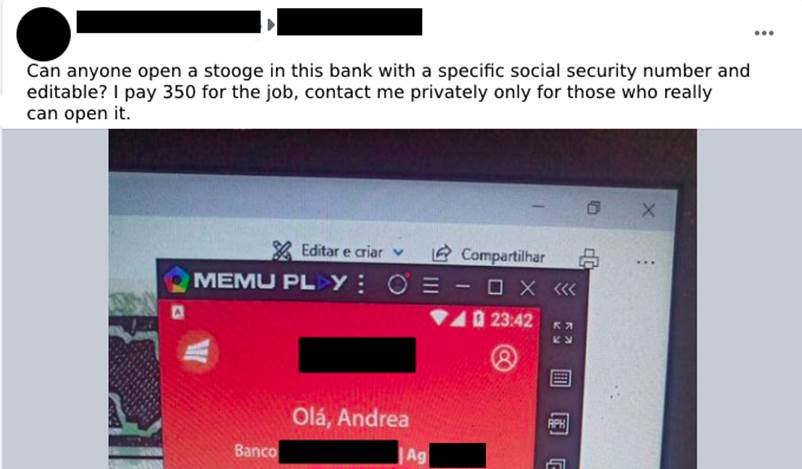
Another aspect of the stooge accounts are the ones opened by scammers using the data of a third party previously selected by the person who is fraudulently contracting the digital account opening service (Images 18 and 19). In this modality, the “customers” search for those who open digital accounts in specific social security numbers and banks with possibly well-defined purposes. These solicited accounts are believed to be for receiving fund transfers from investment accounts, cryptocurrency brokerages, and also bank loans.
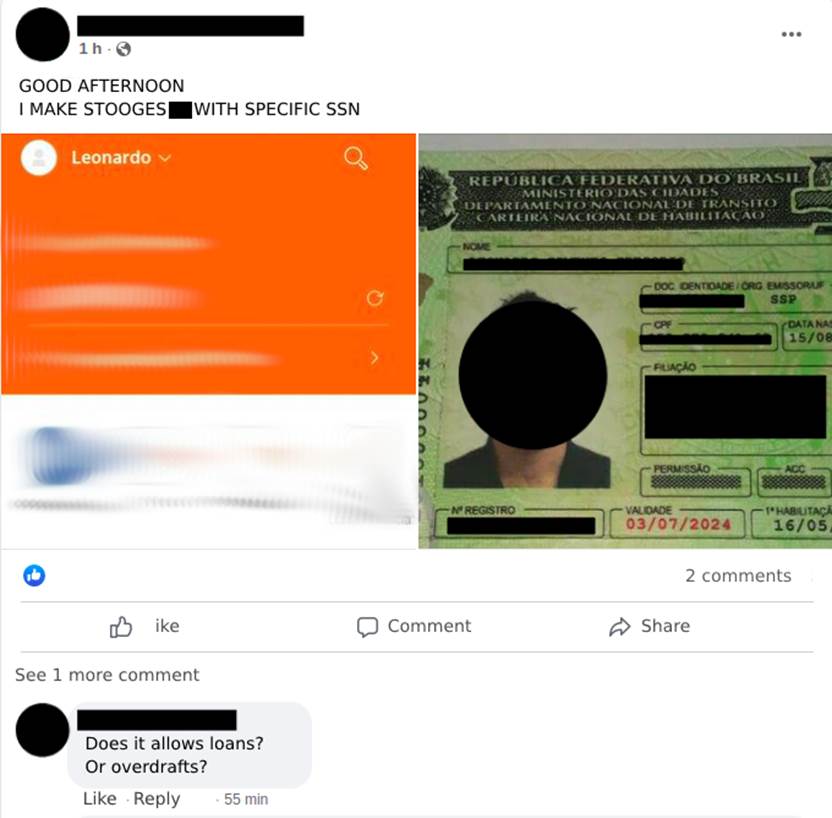
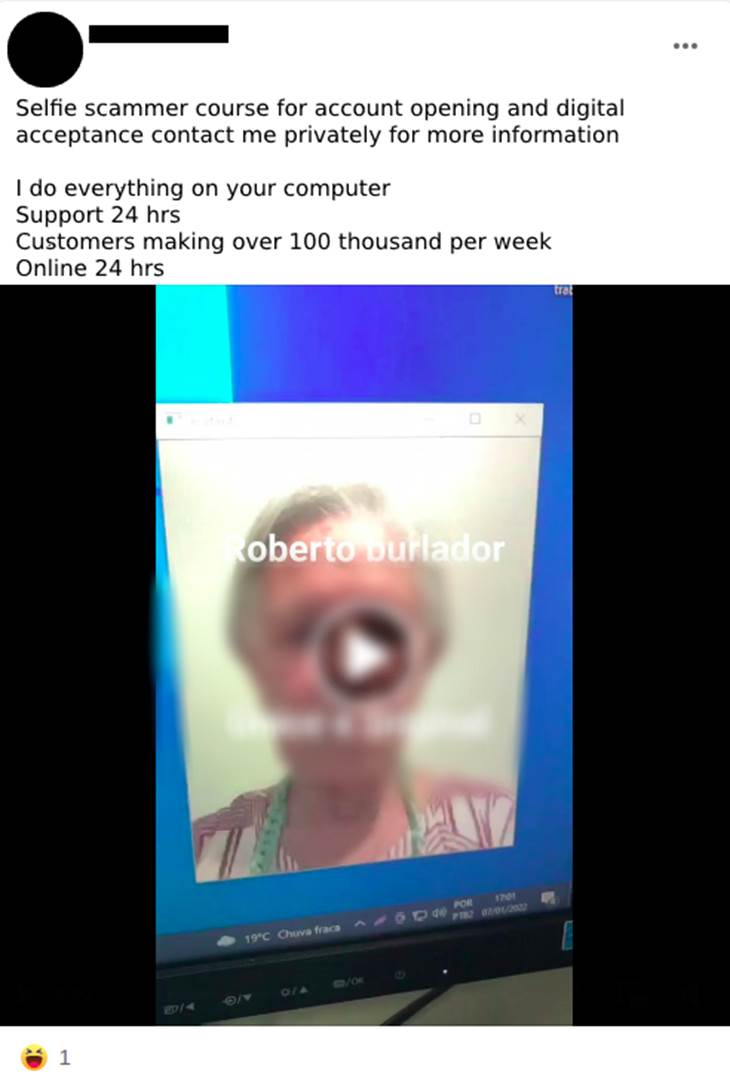
To open such an account, editable documents that look very similar to the original, or copies of the original documents, can be used and are sent to the banks’ applications using modifications in the apps (Image 20) that cause the cell phone’s image gallery to be opened instead of the front camera, so the attacker can select the image of the document previously saved in the device and send it to be validated for opening the account. This process is known among them as “scammer” (Image 21).
3.6 The use of “selfie swindlers” as the icing on the cake
With the popularization of smartphones, banking has become one more tool inside the cell phone and, in this digital world, the opening of a checking account is also widely spread and used. Thus, relations have become more distant between the account holder and the banker, a professional trained to recognize attempts at fraud and scams. Now, machines try to identify if it’s really a genuine person who is on the other end of the machine.
In the beginning, opening an account using a cell phone only required a photo of the documents, but gradually it has evolved to also require a photo/selfie of the account holder, and then a photo holding the holder’s ID or driver’s license close to the face. Currently, one of the biggest advances is the video selfie request (Image 22), in which random instructions are sent to the person who is trying to open the account, such as blinking, smiling, looking up or sideways, and also moving the head in the directions indicated.
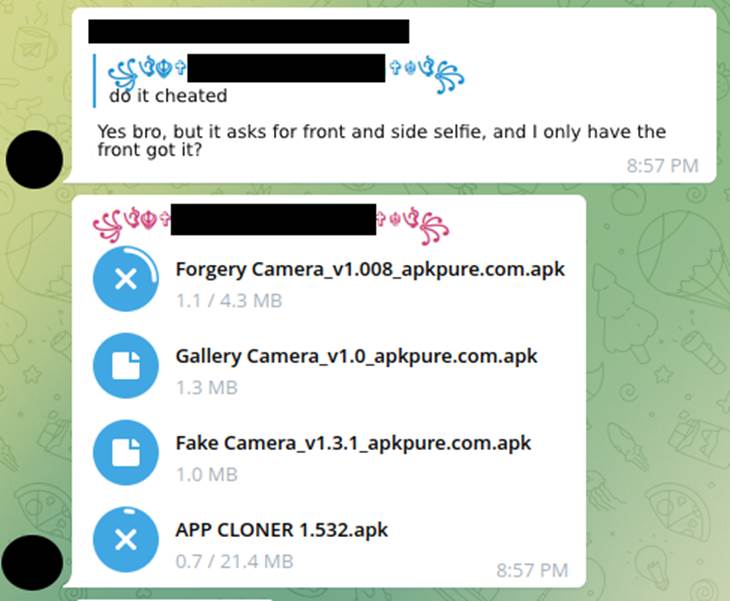
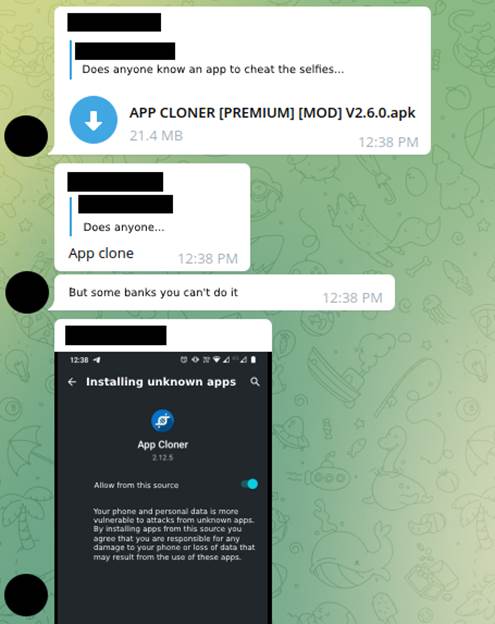
To circumvent the sending of documents and photos the fraudsters resorted to applications installed on the cell phone that intercepted the call from a bank application trying to access the front camera and instead opened the image gallery, among them are: Forgery Camera, Gallery Camera and Fake Camera. However, this was soon fixed in the major banks’ applications so that these simple techniques no longer worked. Then, the use of APP Cloner appeared among cybercriminals, an application that makes a modification of the original APK of the chosen bank. For this, it was necessary to use the application whose main function was to edit the functions of the original application and, thus, open the photo gallery instead of opening the camera for selfie (Images 23 and 24).

Further on it was seen the use of cell phone emulators, among them: MEmu, Android Studio, Bluestack, LD Player, to facilitate the execution of the scams, increasing the scale of the exploits (Image 25). Besides cell phone emulators, other applications, such as ManyCam, are used to emulate a webcam on the virtualized smartphone. Thus, a still image can be sent instead of the photo through the app.
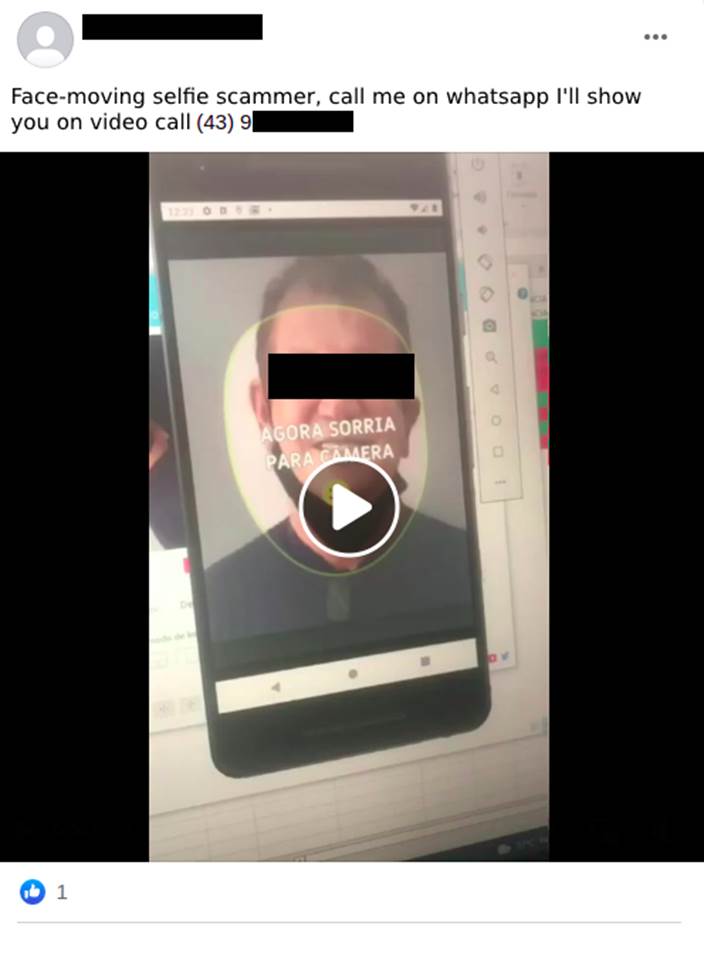
The emergence of proof-of-life validation seemed to be a big hit to fraudsters, since the technologies known and released so far only facilitated subversion using static images. Next came the use of applications that animate photos in real time, such as Avatarify. Now in possession of just a photo of the victim chosen to be the stooge, the attacker can, using his own head movements and facial expressions, impersonate the victim and thereby definitively subvert the validator, by bringing the photo to life.
Given this scenario, new challenges have been imposed to the development teams of digital banking applications. Changes aiming to identify these fraud attempts in the onboarding process or loan formalization, where the software mentioned above and others not so widely disseminated are being used and thus, based on this knowledge, develop more secure and resilient applications in an attempt to identify fraud in proof of life from a remote location, which is a crucial way to protect against the opening of stooge accounts widely used in current scams.
