By Threat Intelligence Team
Last week, Tempest’s Threat Intelligence team identified the spread of the Vadokrist banking trojan through a spear phishing campaign that uses Pix (Brazilian Instant Payment System) as its motto. The threat, which targets customers of major Brazilian banks, uses the DLL Injection technique in its infection process and relies on the GitHub platform to host and query information necessary for the operation of the campaign.
Distribution of the threat
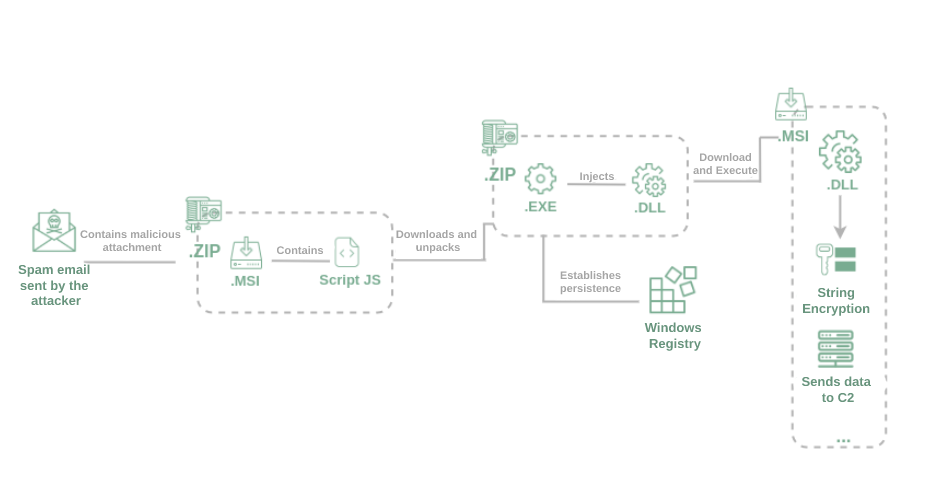
Taking advantage of the popularization of Pix, the operators initiate the distribution of the trojan through a spear phishing campaign that tries to persuade the user to download and execute an attached ZIP file with the promise of protecting the computer against fraud and improper payments. To give more credibility to the social engineering applied to the emails, the operators previously compromised some legitimate domains and made use of the Email Spoofing technique, as well as using newly created domains using the .com.br TLD referencing Pix.

Infection, persistence and command & control
The infection with Vadokrist starts with the execution of an installation file in MSI format, which runs an obfuscated JavaScript script that is responsible for downloading a malicious DLL and a legitimate executable file signed by the company Macro Recorder. This executable injects the malicious DLL into the system through the DLL Injection technique, and then creates a persistence task by adding an entry for a Windows registry key, causing the threat to run with the same permission level as the current user account whenever the user logs into the system. While persistence is created, the injected DLL queries a file hosted on GitHub that contains encrypted strings referring to the command and control server (C2) IP addresses and the download URL of the latest portion of the threat; a second MSI file with backdoor functions that will be downloaded, decrypted and executed by the DLL.
After the infection, the threat remains in “standby mode” waiting for the victim to access the web page of some banking institution that is part of its target list. When this access is identified, communication with C2 is established and the malware waits for the victim to enter the credentials, then captures, and sends them to the server. Besides banking credentials, the Trojan also sends information about the infected machine, such as the version of the operating system, the web browser, the malware that has hit the system, and other things.
String Decryption
To analyze the behavior of Vadokrist, Tempest developed a Python script to decrypt the strings of the malware. This was possible because the algorithm used to encrypt the strings is very similar to that of other Latin American malware families and, in addition, the keys needed for decryption were identified among the malware binaries. Some of the decrypted strings were IP addresses of the servers controlled by the attacker and the download URL of the last part of the threat.
Conclusion
Although the Vadokrist trojan is not widely reported by the specialized media, Tempest has observed a constant update in the mode of operation and in the social engineering applied to the campaigns promoted by this Trojan.
The use of the Pix subject shows the effort of the operators to reach as many victims as possible, expanding the distribution range of the threat. However, Tempest reinforces that this abuse was limited only to the spam campaign, and no processes, strings or any attempts to capture Pix keys were identified at any stage of the malware’s execution.
This new version uses robust obfuscation methods to protect its settings and makes use of a public platform such as GitHub to store, in the form of encrypted strings, the information needed to run the campaign.
Although Vadokrist is aimed at targets in Brazil, Tempest believes that this may become more widespread in future updates, since this Trojan shares many similarities with other malware families targeting Latin America.
IOCs
URLs
[http://13[.]65[.]56[.]28/findP]
[http://157[.]55[.]80[.]194/newT[.]ZIP]
[http://104[.]214[.]65[.]89/JobCompressS[.]ZIP]
[http://summergs[.]worse-than[.]tv/MelaMEOMSJ1029192Ds[.]php]
[http://vaigama[.]scrapping[.]cc/BertolmeLAMES0190[.]php]
[http://vaiost[.]ftpaccess[.]cc/Vasftlomber901gtdma[.]php]
Github
https://github[.]com/rodolfocarlos/produtcs-api
[https://raw[.]githubusercontent[.]com/rodolfocarlos/produtcs-api/main/updater[.]md]
[https://github[.]com/rodolfocarlos/produtcs-api/blob/main/DISCOVERYP[.]md]
[https://github[.]com/rodolfocarlos/produtcs-api/blob/main/DISCOVERYM[.]md]
[https://github[.]com/rodolfocarlos/produtcs-api/blob/main/DISCOVERYL[.]md]
E-mails utilizados no spam
IPs
104[.]41[.]1[.]116
35[.]223[.]36[.]252
151[.]101[.]0[.]133
13[.]89[.]234[.]31
191[.]234[.]186[.]245
70[.]37[.]101[.]247
20[.]52[.]58[.]124
Hashes
Filename: PIX-SEC30.ZIP
Md5: 1854de6a97f87bc723011722e799d016
Sha1: c6644ea2d60762b209bef23905bfa226f7be7d11
Sha256: 3b4f844359e5af7a78da08293f4d29bb1c301c3a12159f98e2a8820e91ebe7c4
Filename: PIX-SEC30.msi
Md5: 6fd80f160afc4641fce125735d32d065
Sha1: 63cae2b9a36f42355d4b09849668a0ec661137e8
Sha256: fb240b75af99c31735eae08e5d1f631d6932268dcfae290058bab4e483743040
Filename: Keys Recorder15.ZIP
Md5: 6892225255a998ad93b82ab740fab072
Sha1: c6ecf20a88079ea4c09a0f9cbea95fa9d5011e5c
Sha256: d321a2472e99fa6f41128cca7d671f1e1561003c004162acbc7fe61a878c73da
Filename: MacroRecorder.exe (Binário legítimo)
Md5: 67ced7026bfe75d93263a70fdef5b9c5
Sha1: 9673baf1ee29d2d2a8176715c3e6c6f54140d95f
Sha256: 93a359ddf66b4867493e6c5a90cf607da2b45bc83f1ce740aa1c7cdb0131244e
Filename: mrkey.dll
Md5: 14336c3ba1a725c2ea035ac251724445
Sha1: 526faed6e386fc4cc0a367488a4b3874c59cec1f
Sha256: 83d9aca673ae2415b57d7c631be1334d4259cc00aee17f84d710868a1186f377
Filename: findP.msi
Md5: 4294c873d792baf09b747b07cccefc01
Sha1: 3e7a69ea1a34361eaa94d4e4744d560edacaa268
Sha256: 48f8d0ccded94533fd38b98031e31187c49728314015cdb09c48ed79dc474dae
