By Threat Intelligence Team
Tempest’s Threat Intelligence team recently identified a campaign to spread a new variant of the Mekotio banking Trojan against targets in Latin America, particularly in Brazil. The latest version features significant changes in its infection process that have been segmented into several stages and in its use of features to evade detection mechanisms and expert analysis.
Trojan Features
Mekotio is a Remote Access Trojan (RAT) whose primary functionality is financial information theft. Experts believe that this Trojan family originated in Brazil; however, there is no consensus on when this malware appeared. According to the company FireEye, the activity of this Trojan started in the middle of 2018. ESET believes that the threat has been active since 2015. Initially, Mekotio’s targets were located exclusively in countries in Latin America, such as Brazil, Chile, and Mexico, but in 2020, the threat started to target countries in Europe, such as Spain.
Recent changes in the threat’s operation also extend to technical tactics and procedures (TTPs), such as employing a custom encryption algorithm, abusing legitimate operating system binaries (LOLBins), and adding useless bytes.
Campaign
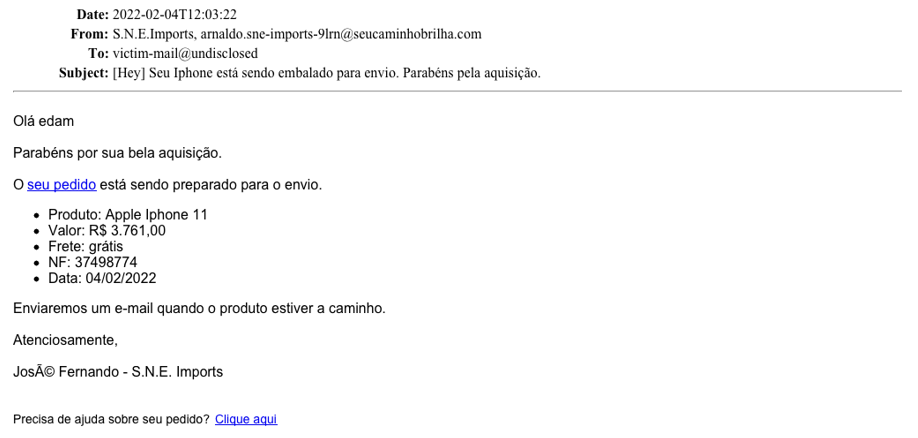
During February, Tempest honeypots registered about 14,500 e-mails distributing the Mekotio variant. The messages are constructed with the intention of exploiting the victim’s curiosity by informing them of the imminent shipment of a product purchased over the internet. In the body of the message is a URL generated via Azure services that take the user to an Amazon Elastic Compute Cloud (Amazon EC2) instance, which stores a downloaded ZIP file.
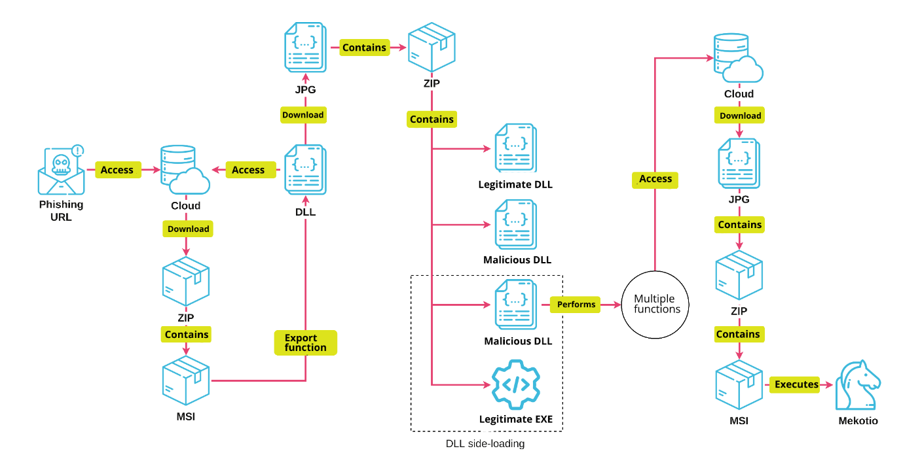
Stages of Infection
The Mekotio infection is divided into three stages, in which MSI files execute the entire chain using functions exported from DLL files via CustomActions – personalized actions that can be configured and executed during the MSI installation process. These functions are used to download, extract and run the payloads from each stage, inject the malicious DLL using legitimate binaries (DLL side-loading), and configure persistence. The files used at each stage are downloaded from cloud platforms such as AWS and Google Drive in JPG image format. These images are then processed to reveal MSI files and other artifacts.
First Stage: Dropper
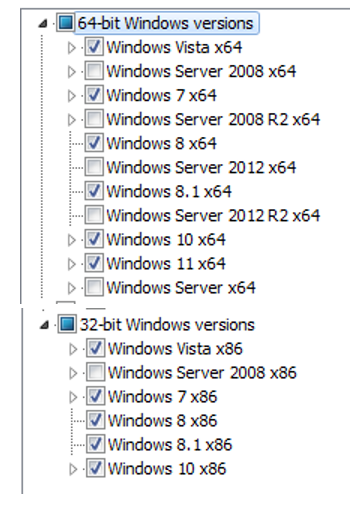
Once the ZIP file is downloaded through the link in the e-mail, it’s necessary to extract it, returning a randomly named MSI file (jvyq.7.yf3c7prvx.msi) responsible for the first stage of infection. Inside the MSI it was possible to observe that the file was configured not to run on any version of Windows Servers present in the market:
This MSI has a CustomAction that has the function of loading a DLL file (jump_force_deluxe.dll). The MSI uses the CustomAction to execute a function exported by the DLL called “SDL_AudioStreamClear”. This function is used to download the second stage of the malware infection and allocate it to the respective folders.
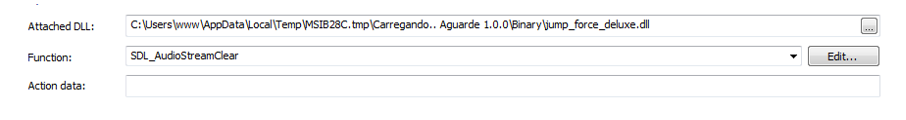
Before performing any action regarding the acquisition of the second stage, a check is performed. The DLL present in the first MSI analyzes whether inside the folder C:\Users<USER> there is a directory with the local user’s name. The DLL will not execute the second stage download if it exists, thus serving as a KillSwitch in the infection process. If it doesn’t, then the download is executed.
The function exported by the MSI accesses a URL to perform this download. This access causes the victim’s computer to receive a JPG file extension, and the exported function is responsible for extracting a ZIP file from within the image.
Upon decompressing the ZIP file in memory, the function creates a folder with the same name as some software present inside C:\ProgramData and allocates the four received files inside it. This folder is then placed inside C:\ (Local Disk).
The files in question initially use the extension BMP (1img.bmp, 2img.bmp, 3img.bmp, 4img.bmp). The function is then responsible for renaming the four files allocated in this folder to a file with extension EXE ( the name is configured randomly) and the other three with extension DLL (names configured by strings fixed in the DLL of the first stage), where two are malicious: vstdlib_s.dll and PSVirt32.dll. The other DLL present is only for starting the execution of the legitimate software that came bundled with this download:
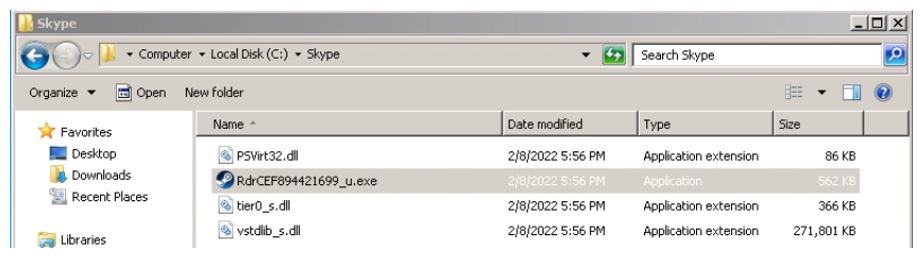
MSI also inserts a scheduled task using schtasks.exe, which will be responsible for starting the second stage. The scheduled task serves to start the legitimate executable mentioned above. This task will be programmed to run only once with a specific date and time (the time will always be approximately 3 minutes after the MSI has been executed)
Stage Two: Preparing the environment
The legitimate executable in question is a module present in the Steam software. The name came up as RdrCEF894421699_u.exe. However, the executable is known in the market as steamerrorreporter.exe and is used in the second stage of infection to perform a technique known as DLL side-loading. In Windows, programs can define which libraries are loaded at runtime by specifying a full path or using other mechanisms. The DLL side-loading technique aims to take advantage of weak library references and the standard Windows search order by placing a malicious DLL file disguised as a legitimate DLL on a system, which will then be loaded automatically by a legitimate program. The first place that Windows will search is the directory from which the application is loaded, which is what happened in this case.
When the vstdlib_s.dll file is started via DLL side-loading, it calls the PSVirt32.dll file, whose mission is to perform a number of functions responsible for checking the current environment is a VM (Virtual Machine). The DLL performs several system checks to detect and avoid virtualization and analysis environments well-known on the market, such as VirtualBox, Wine (compatibility layer for UNIX operating systems that aims to implement the Microsoft Windows API), VPC (Amazon Virtual Private Cloud) and VMWare.
The second action performed by the vstdlib_s.dll file is to add the call of the legitimate executable to the Run registry key within HKEY_CURRENT_USER, causing the file to be executed every time the infected user is logged on.
Soon after, the file creates a sub-process running the WMIC.exe. This executable is a command-line utility that is used to access Windows Management Instrumentation. Windows Management Instrumentation (WMI) serves as an infrastructure for management data and operations in Windows-based operating systems. The file takes advantage of this tool to obtain information from the operating system and to obtain a list of the Antivirus present on the infected computer.
Third stage: Mekotio
The previous infection stage leaves stored in the Documents directory of the infected user a file called “nimda”, which is nothing more than the user’s name backwards (“admin”), with extension ini. The file serves as a kind of validation where the next steps will only be carried out if this file is present on the computer. This file has as information the version of the threat to download, the date of infection and the folder in which to store it:
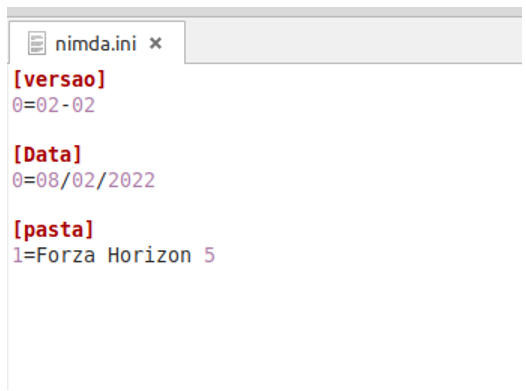
After performing the validations mentioned in the second stage, a new download is requested by the DLL vstdlib_s.dll. The downloaded file is nothing more than a JPG image that has an encrypted URL concatenated to the end of the file. The DLL then removes the encryption and again performs another download. A ZIP file is then acquired, containing an MSI. The memory-stored ZIP file is then extracted, and the MSI is stored in the directory below and saved with a random name (1643afvc.msi). This MSI has a bundled DLL containing the Mekotio:

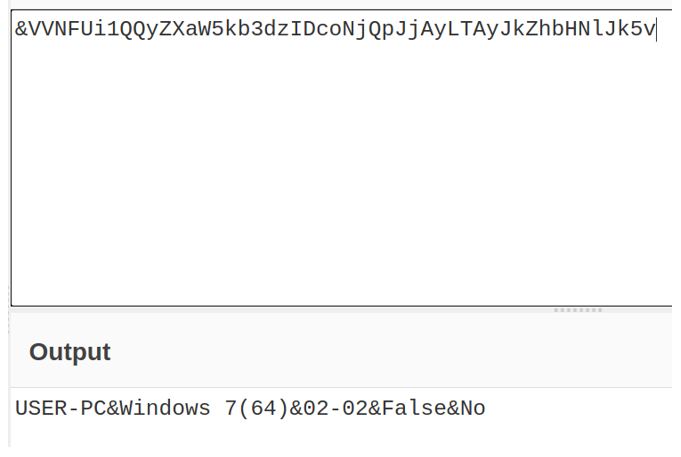
The same DLL subsequently accesses a URL containing Base64-encoded string parameters. The string sent, coupled with the counter parameter, forwards to the victim counter the name of the computer and its operating system, plus the “False” and “No” strings, which refer to the Antivirus check done using the WMIC.exe, and a confirmation whether the computer has ever been infected by this sample:
After performing the steps above, the file creates a MessageBox, informing you that the computer will be shut down. Then a child process is created, executing the file shutdown.exe, thus restarting the computer, as shown below:
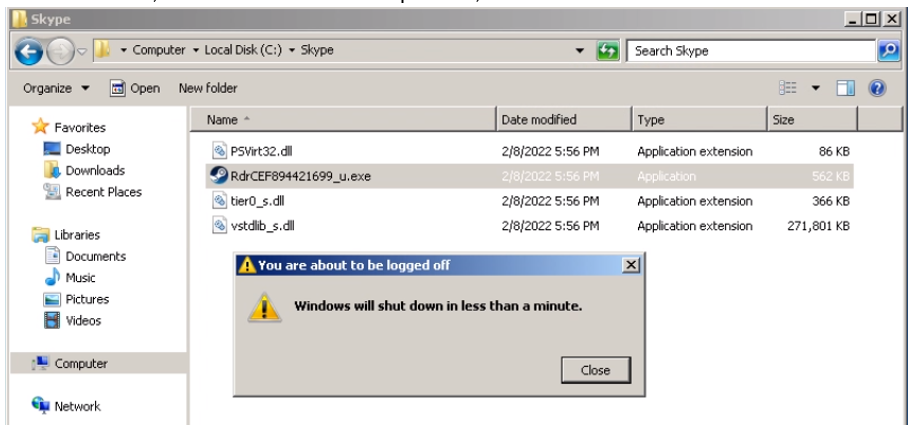
When the computer turns on, the file RdrCEF894421699_u.exe is started, and the DLL side-loading is repeated. This executable again uses the WMIC.exe to check if there is any antivirus product installed on the device, and if no antivirus is detected, a subprocess of the executable msiexec.exe is created by the file in order to run the MSI that was stored in the Forza Horizon folder:

Mekotio: Inside the Threat
The analyzed malware has several encrypted strings. However, the decrypting of the strings used by the threat was done by understanding the custom encryption algorithm. By decrypting the strings, it was possible to identify a lot of information about how the malware operates. The malicious DLL in question has text that is possibly used to persuade the victim to re-enter the submitted information, report that the site is updating, report that the system is being restarted, and instruct what security measures are being taken.
The mekotio also has strings referring to Internet banking software, which are probably used to identify their presence in the victim’s environment. Some specific functions were also found to be executed on the infected host, all of which are designed to control the computer. Within its encrypted information, it was possible to observe that the threat focuses on individuals and companies and also contains a list of targets covering Digital Banks, cryptocurrency trading companies and Latin American banks in general.
To establish a connection to the command and control server (C2), the malware accesses a Dropbox URL to download a ZIP file that contains a JPG image. This image has a series of encrypted data (using the custom algorithm) that, when decrypted, reveals the IP address and port of the C2 server. All communication is done in an encrypted mode, and the malware sends “PING” strings to the C2 and expects to receive a “PONG” return to confirm that the computer is still infected and operational.
Analyst Commentary
The new variant analyzed by Tempest features significant changes in its TTPs. In previous versions, the stages of infection were not very elaborate, while in the latest version, there are successive pre-infection steps that create a real puzzle until the malware is implemented. In addition, the Trojan has made massive use of CustomActions to export functions from malicious DLLs. Since CustomAction execution is done directly by the msiexec.exe process, identifying these malicious DLL calls is a challenge for analysts. Some functions present in older versions of Mekotio still remain active. However, new tricks have been identified, such as using the schtasks.exe to schedule tasks, employing a custom encryption algorithm to obfuscate the name of target institutions, malicious actions and communication with the C2, and modifying the structure of image files to concatenate data.
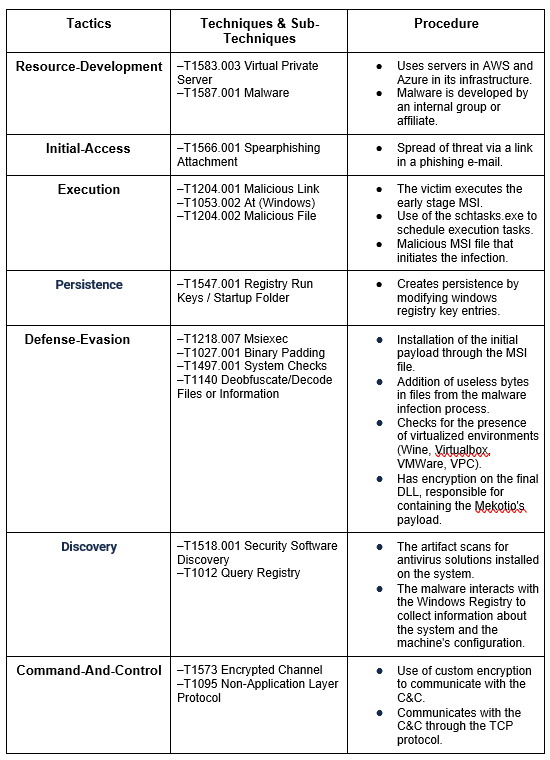
MITRE ATT&CK