By Threat Intelligence Team
The pandemic caused by the new Coronavirus has caused long quarantine periods worldwide. As a result, the need to migrate activities and services, which were previously partially or totally on-premises, to remote platforms was intensified. Services from the retail, financial and customer service sectors – which had already made their activities available over the Internet – migrated almost exclusively to the digital environment, taking millions of users with them.
Although there are specific platforms for companies to offer their services, it’s common for some users to seek assistance through company profiles on social networks, responding to publications on Twitter or commenting on Facebook or Instagram posts about a specific problem, for example. Observing these movements, criminals create fake profiles to identify and approach customers from different companies, or simply wait for the victim’s contact, aiming to conduct various attacks based on social engineering, ranging from the hijacking of WhatsApp accounts to the execution of frauds and information theft.
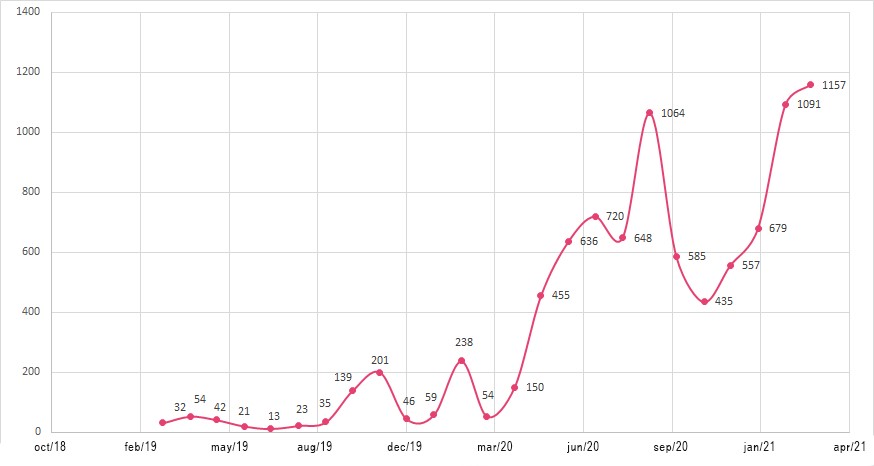
At least since 2014, Tempest‘s Threat Intelligence team has been monitoring this category of targeted scam which is known as “Impostor Attendant”. Even though it’s not a new form of attack, it has become popular during the pandemic period.
According to Tempest‘s detection mechanisms, there was a significant increase in the number of incidents related to fake profiles on social networks and, within this category, profiles related to Impostor Attendant scams.
Scam Operation
In an analogy, what we call the Impostor Attendant is essentially an Internet adaptation of the traditional scam in which the fraudster addresses people in line at the ATM posing as a bank employee and offering supposed help to people with difficulty using the system. However, if in the physical version of the scam, the main objective is to clone the victim’s card, the virtual modality offers a greater range of possibilities.
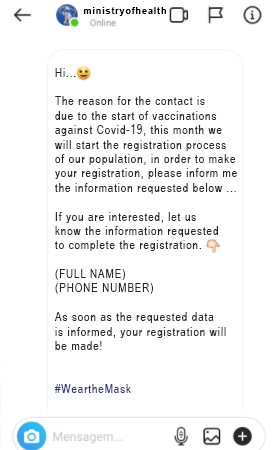
Criminals create fake profiles using names and logos very similar to those used in the legitimate profiles of the target companies, and can conduct the attacks passively or actively. In passive attacks, criminals create the fake profile and try to imitate the behavior of an official account of the institution, posing as representatives to gain the trust of users and get them to contact in search of assistance.

Comparison of timelines of the official profile of the Brazilian Ministry of Health (left) with a fake profile (right). Image: Tempest.
In the active approach, criminals monitor consumer interactions with legitimate profiles of institutions, approaching customers who try to contact them to answer questions or seek assistance. It’s common to use terms such as “CSC”, “customer service” or “support” when creating these profiles.

After making contact, the attack can proceed in several ways. Fraudsters often hijack the victims’ WhatsApp account, asking them for a fake confirmation code for identity validation, which is actually the app’s authentication token. Once in control of WhatsApp, criminals extend the blow to people on the victim’s contact list, inducing them to make loans and financial transfers.
Due to these characteristics, WhatsApp account hijacking scams are more attractive to criminals with little technical know-how, since it’s not necessary to know any programming language or to know network protocols, for example, to obtain financial income.
Theft of personal data, including images of users’ documents and selfies, is another common monetization strategy. These photos are used to obtain loans on behalf of the victims or are resold to other fraudsters. Even simple data like email and phone numbers have value in the underground data market. In 2018, Tempest detailed how the theft and negotiation of this data occurs in the document fraud survey.
Another type of fraud consists of redirecting the victim to malicious websites that can simulate virtual stores and generate payment slips for products that will never be delivered or, in the case of financial institutions, collect Internet Banking credentials. Scams related to the generation and sending of false “duplicate bills”, have also been observed frequently.
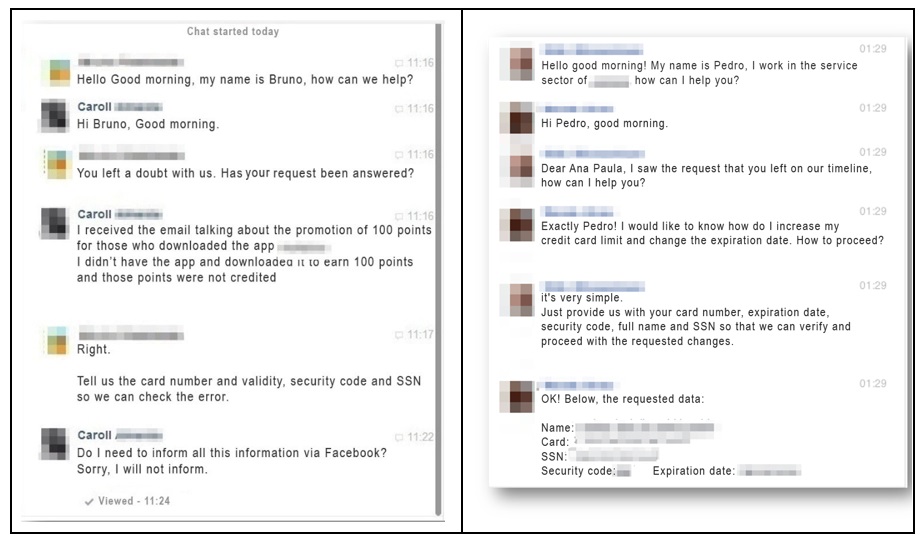
Two cases in which the attacker seeks to obtain the victims’ credit card details. In the image on the left, he does this by posing as an attendant at a mileage company, in the case of the right posing as a bank employee. Image: Tempest
Finally, in some attacks, especially those in which criminals pose as technical support, users may be persuaded to install malicious programs on their devices, which could lead to compromised home and corporate networks in more sophisticated attacks.
Technique exported to other countries
Recently, the activity of attackers using the Impostor Attendant technique in other parts of the world has been documented: On April 1, Group-IB published details of a campaign using Attendant Impostor attacks against banks in Indonesia. The attacks begin with the identification of customers responding to publications on the banks’ official Twitter profile. After making contact, operators take the communication to another platform, such as WhatsApp or Telegram, then direct the victim to a fake website abusing the institution’s brand to steal users’ credentials.
On the 5th of the same month, eSentrire published details of a campaign being conducted from LinkedIn profiles offering fake job openings aimed at infecting users with a backdoor, nicknamed “more_eggs”. Criminals disguise the malware files using job titles of interest to victims.
The Google Threat Analysis Group recently identified a fake cybersecurity company created by a North Korean APT group. At the time, it was possible to link the criminal group to the company thanks to a public PGP key available on its website, which was also used in previous attacks. Entitled “Securielite”, the company has fake profiles of users on LinkedIn claiming to hold positions in the company. Possibly, these fake profiles would be used to approach researchers and security experts, since the same group has already been observed acting against these professionals.
Social Networks
Malicious activities on social networks cover part of the OSINT process that is often necessary to conduct an attack, considering that users share their personal and professional interests on the network, in addition to interacting with companies of which they are clients.
A feature that attracts criminals to this type of scam is the ease of reaching their targets, unlike spam campaigns, for example, in which criminals need a predefined target list and the ability to bypass email filters to reach their victims, in addition to an infrastructure capable of sending malicious messages, which can be more costly in some cases. In Impostor Attendant scams, criminals only need to monitor public account activity and wait for the easiest targets to identify themselves when interacting with the official pages of entities of interest.
The difficulty in assigning responsibility for this type of attack is another point that deserves attention, as the accounts used by criminals are usually disposable. That is, after using the fake profile for a few days or hours, criminals abandon or remove these accounts from the platforms, making it difficult to identify them. In addition, there’s a great difficulty in the identification of this type of scam by the institutions, since generally, it happens in the interaction between “Victim and Fraudster”, not necessarily passing through any channel or platform of the target institution, which often only takes notice of the attack when they receive the complaint from customers who paid a fake ticket, for example.
To avoid falling into this type of scam, it’s important for users to know the media and the official profiles of the institutions. Always be suspicious of profiles that come in contact under the pretext of providing support, especially when sensitive information is requested to conduct the procedure. It’s also necessary to exercise caution when clicking on links, especially those provided by suspicious profiles, since the use of fake pages is one of the strategies adopted by these criminals.
Final Considerations
It’s challenging to control criminals’ access to the ability to publish content using these pages without losing the marketing purpose that social networks offer. The ease of access and the anonymity that the coup modality allows, limits the options of companies in combating this type of activity.
Thus, the viable and most efficient option is the effective dissemination of the official communication channels to its customers and partners, seeking to convert the profiles into accounts verified by the platforms and carrying out awareness campaigns in order to contribute to the dissemination of knowledge about the potential offensive of these malicious practices.
The active monitoring of Threat Intelligence services in search of fake profiles, the activity of Takedown and the identification of new forms of this and other scams, also play a crucial role in combating this type of cybercrime.
Tempest works together with the main social media platforms to combat this type of scam on its customers, monitoring, identifying and acting on the removal of these fake profiles.
