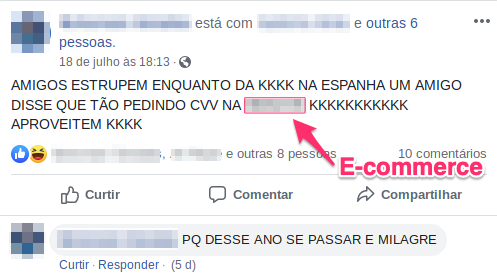
Tempest’s Threat Intelligence team has been monitoring the activity of Brazilian fraudsters groups who are negotiating ways to obtain card verification value (CVV) through the automation of distributed tests. The service is advertised in several channels and promises to obtain the verification code of a card in up to five minutes, allegedly considering a deliberate delay in the test execution aiming to circumvent fraud monitoring mechanisms.
The flaw exploited by the fraudsters is related to the way the payment card industry is organized and has already been identified by researchers Mohammed Aamir Ali, Budi Arief, Martin Emms and Aad van Moorsel from the universities of Newcastle and Kent in the United Kingdom. In a 2016 study, researchers tested the industry’s ability to identify the attempt to obtain CVV data via brute force by sending up to 999 transactions from 342 different e-commerce stores.
In fact, researchers were not only able to “guess” the CVV, but, from a set of card numbers, they obtained the card expiry date and the cardholder’s postcode number, information that can be used to identify the cardholder on e-commerce.
There is no evidence that Brazilian fraudsters have studied the Newcastle and Kent paper. However, considering that the number of attempts to obtain this information from a set of websites does not represent a major computational effort, its execution becomes an obvious consequence, and the Brazilian fraudulent operation relies on additional resources, something that the British research from three years ago could not predict.
Obtaining card numbers and expiration dates occurs essentially through attacks and leaks, but many fraudsters have noticed that some issuers may have misconfigured systems, making it possible to execute transactions using card numbers that do not exist, and are created using the Luhn algorithm — a default format adopted by the industry — from a BIN (Bank Identification Number) known as vulnerable. This means that, from the first six digits that identify an issuer that accepts card transactions using card numbers that have not yet been issued, fraudsters use Luhn’s algorithm to create the other digits of the card. It is common to find tools that automate the work and can be hired as a service. Brazilian fraudsters often call these cards “geradas” or “gg”.
Issuers that do not validate whether the card number exists may also not check the expiration date. The fact that cards are commonly valid for 60 months helps fraudsters to limit the scope of possible expiry dates, increasing the possibility that their “geradas” (generated) base will be considered valid. Tempest’s threat intelligence team has already identified cases where there is not even card verification value validation.
Although it is still possible to identify fraudsters saying that they have found merchants or issuers that do not block the use of “geradas” or that allow for transactions to be sent without the card verification value, the number of industry entities with misconfigured systems is becoming scarce. That is why it has become necessary for criminals to diversify their efforts, “guessing” the CVV for legitimate cards by other means.
In the 2016 study, researchers created an application to legitimately submit transactions with their own cards in more than 300 e-commerce stores, and each successful transaction would denote that the “guessed” CVV was correct. Brazilian fraudsters, on the other hand, have more resources at their disposal.
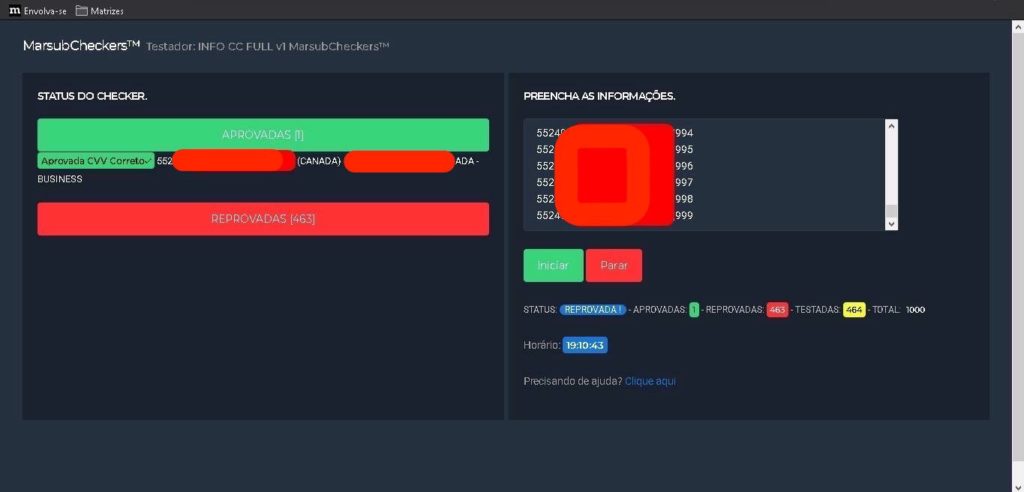
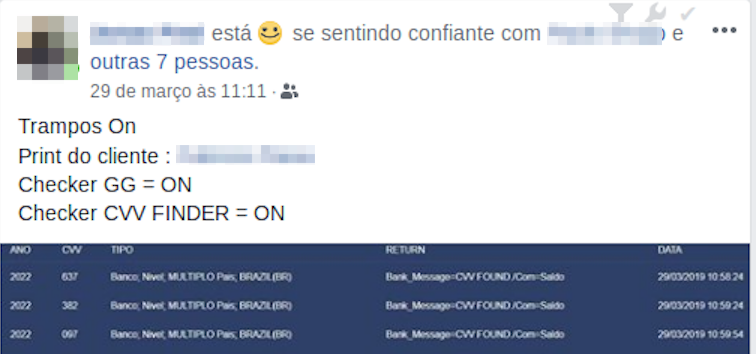
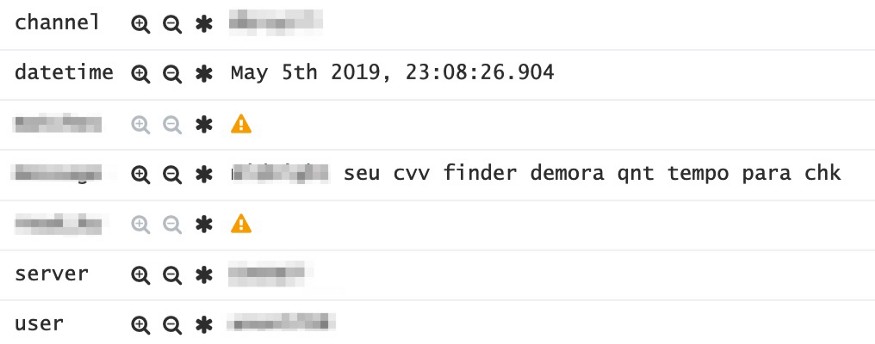
Based on the card number and expiry date, the search for a CVV can be done by sending automated transactions originating from several stores. The type of software that performs this function has been named by Brazilian fraudsters as Finder or CVV Finder.
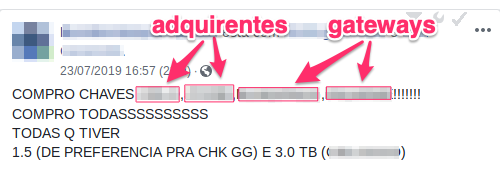
In order for the search to become possible, the fraudster uses legitimate e-commerce stores, previously identified as misconfigured, and fraudulent online stores, but which are registered with acquirers and payment gateways through the use of false or stolen documents. Mule’s documents are also used to reregister fake stores.
Another way to submit multiple transactions is by emulating multiple stores through the use of stolen keys from payment gateways or acquirers that are negotiated between fraudsters. The keys are formed by a string of characters with the function of authenticating transactions that originate from a company that intermediates transactions of several e-commerce stores.
Obtaining the CVV through both techniques, abusing e-commerce or using stolen keys, is something done by means of automated checking of the output received from the payment gateway or from the acquirer (see table below). If the answer is that the card verification value is invalid, this would be a sign that the card number and the expiry date are OK, so the system just continues testing the CVV until it gets the correct information.

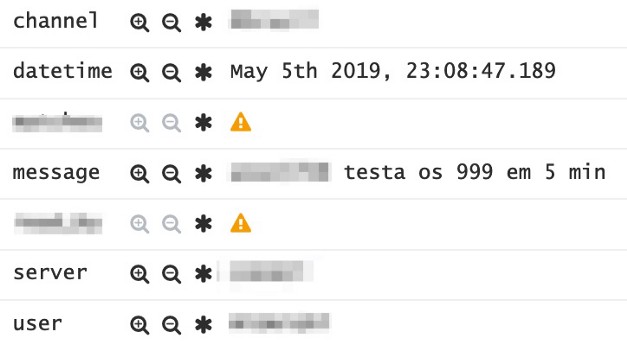
To obtain the CVV of a card which information is based on 3 digits, 999 attempts are enough, an elementary effort for a system prepared for this. Newcastle and Kent researchers were able to obtain this information in 6 seconds; however, Brazilian fraudsters say they execute the process in 5 minutes, allegedly in a deliberately delayed operation to avoid identification of bursts by anti-fraud systems.
According to the British study, the problem occurs because there are few centralized monitoring points in the payment card industry and because there is a need for the industry to unify controls globally, because there are still e-commerce stores through which it is possible to send transactions without the card verification value, for example.
The payment card industry has developed into a complex and distributed design, in which it does not matter how much each entity takes care of its own security, still few of them have a broad view of what is happening in the network.
Some organizations avoid implementing security measures that could become an obstacle for impulse buying, tolerating a certain level of fraud in order to maintain the volume in sales. This is an approach that is part of many businesses, but it is recommended that entities at the top of the chain, which deal with the largest volume of transactions, reassess the multiplicity of double standards situations, seeking for an acceptable minimum.
According to the research, it is within the payment network — which involves acquirers and payment brands — that there would be more chances of applying centralized monitoring, being able to identify several transactions with the same card number, but with a different card verification value, originating from several merchants.
This kind of monitoring and blocking already exists. One of the payment brands tested in the 2016 research was efficient in identifying and blocking malicious attempts, but the evidence that Brazilian fraudsters are obtaining card verification value data in similar attacks shows that there is much to do in order to unify controls and centralize monitoring.
It is recommended that, in addition to reassessing monitoring, the payment network monitors the behaviour of the gateway. For issuers and e-commerce stores, it is important to evaluate the implementation of new technologies developed by payment brands or by the market (e.g., contextual authentication or the use of the bank’s token to authenticate an online transaction), thus offering better ways to validate whether the person submitting the transaction is really the cardholder.
