This article aims to provide an overview of scams via WhatsApp that have increased a lot due to changes in the way of consumption, and in the population’s work model, as a result of the Covid-19 pandemic. Below, we’ll discuss ways to prevent variations in this type of fraud and what you can do if you become a victim.
WhatsApp account hijacking is a scam that has been around for a few years. The first frauds were identified in mid-2016 against customers of e-commerce sites in the consumer to consumer (C2C) mode and worked as follows: the attacker collected the ad information, contacted the user and, through social engineering, said that to activate the ad it would be necessary to inform the code received via SMS.
Social Engineering, in the context of information security, is a set of techniques that aim to deceive people, through psychological influence, to obtain valuable information, with the manipulation of human feelings being one of the most used devices by criminals, as a sense of urgency, the perception that an advantage is being taken of something and, above all, curiosity.
Methods
Cloning via verification code
In this type of scam, the goal is to capture the WhatsApp verification code and, to accomplish this, the criminal invests in different approaches to social engineering, the aforementioned being the most common.
In general, the scammer offers a promotion with apparently irrefutable advantages, however, to release the purchase, coupon or any other product, he says he needs the 6 digits he just sent via SMS. When the victim provides this number, expecting to receive the promised benefit, he is actually sharing the WhatsApp verification code with the scammer, which is used to access the account on another device.
Another variation of this modality, called the Imposter Attendant, focuses on the official pages of financial institutions, through which the fraudster monitors customer complaints, and gets in touch posing as an attendant or as a bank manager, stating, among other things, which to avoid blocking the application, it’s necessary to inform the six-digit code that was sent via SMS.
Another approach, which explores themes related to the Covid-19 pandemic, is based on the narrative that the fraudster would be a health agent who would be doing research for the Ministry of Health.
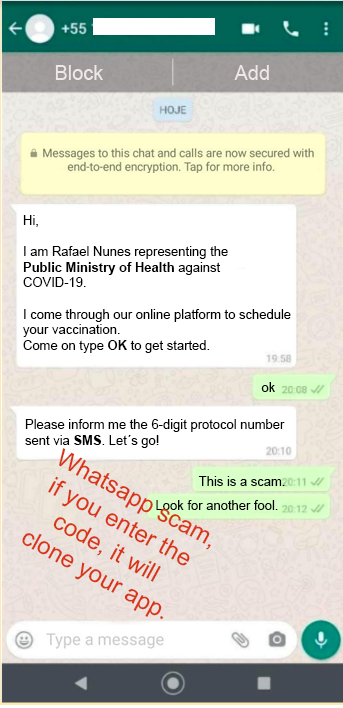
The only way not to fall victim to the “Imposter Attendant” approach is to be suspicious. If they get in touch to solve a problem requesting codes or personal data. In these cases, it’s recommended to get in direct contact with the company’s SAC by telephone or e-mail, as companies usually do not ask for an authentication code via SMS for these functionalities.
SIM Swap
This scam consists of hijacking the victim’s cell phone chip number, linking the number to a new chip, and consequently a new cell phone, owned by the fraudster. This hijacking of the line can happen momentarily or permanently. In order to make the exchange, fraudsters buy a new chip and use social engineering techniques against mobile phone operators or their service providers, contacting and posing as the owner of the original chip, stating that their device was stolen and requesting number portability to another device. Another technique also used by fraudsters is the realization of document fraud – presenting false documents.
In some cases, the fraudster can also count on the support of employees of telephone companies or represented companies that participate as accomplices in the scheme, who have access to restricted systems of the operators to make the changes. There are also scenarios where fraudsters are able to perform SIM Swap using credentials to access the operator’s systems that have been leaked or stolen.
To perform this procedure, the fraudster only needs the victim’s cell phone number, full name and date of birth, information that can be easily obtained on the Internet. After the process, the original chip is deactivated and the fraudster gains access to the victim’s contacts and groups on WhatsApp.
It’s worth mentioning that the act of unlinking an account to a chip and linking it to another, is a process normally used by operators to serve customers who buy a new device or who had the device lost, stolen or broken. The SIM Swap scam already has 8.5 million victims in Brazil.
With the recent leaks that occurred in 2020 and early 2021, which were widely reported by the press, fraudsters have enough data to try to apply the SIM Swap against multiple consumers, which demands extra care from telephone operators and attention to instabilities in the service by users.
Monetizing the Attack
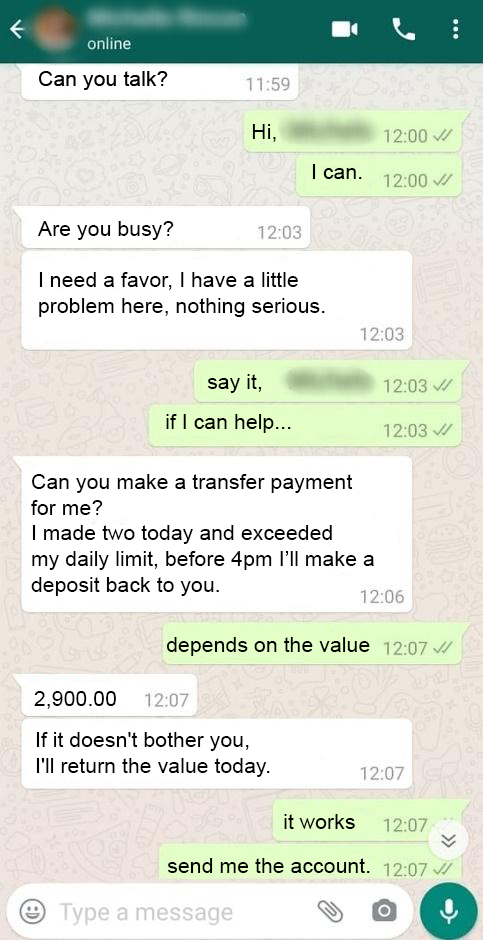
Many victims don’t realize that the code provided to the criminal is the application’s authentication code and, by handing over this access key, they allow the fraudster to connect to their WhatsApp account on another device. As a result, the victim often loses access to the account. Then, the fraudster approaches the contact list looking for family and friends in order to make new victims, saying that he needs an urgent transfer and informs his bank details, as we can see in the following case.
How to protect yourself
There are two measures that can be used to avoid these scams, the first is never to share confirmation codes received via SMS to third parties. Last, but not least, is the activation of two-step verification, a feature provided by the application itself in Settings/Settings > Account > Two-Step Confirmation > Activate.
With this feature enabled, you’ll need to enter a six-digit password every time the app asks for confirmation of your phone number. This means that if a criminal tries to hijack your WhatsApp account, he’ll still need this code to use the account on another device.
Although these features increase your security, it’s necessary to take other preventive measures, such as avoiding clicking on suspicious links sent by messages in groups or via SMS and not installing applications from an unknown source or originating from unofficial stores, since this type of action can allow the execution of other types of attacks, such as the installation of malware, especially those aimed at stealing personal and banking data.
What to do after having your WhatsApp attacked
The first thing to do after identifying that you were a victim of the scam is, if possible, to contact family and friends to alert them, this way you can prevent financial transactions from being made to the fraudster.
Then there are two scenarios to consider, in the first one, the account doesn’t have 2-step verification enabled and the criminal, after hijacking it, didn’t enable this functionality. In this case, try to recover your account, as this way, it’s possible to disconnect the scammer by installing the app again and entering your phone number and the new verification code that will be sent by WhatsApp. With that, whoever is using the account will be automatically disconnected.
In the second scenario, the account doesn’t have 2-step verification enabled and the criminal has activated the feature after hijacking the session. In this case, following the same steps, the fraudster will be disconnected, however, the victim will only be able to access his account again after seven days.
In cases of SIM Swap, the steps above will have no effect, being necessary to buy a new chip and activate it with the operator.
Other important steps to be taken after identifying the scam are:
- Register a Police Report;
- If any person has made a transfer, notify the financial institution;
- Send an email to [email protected] requesting the fraudster’s access to be disabled;
Impacts
The main impacts involving Whatsapp account hijacking fraud are: Leaking private and confidential conversations, sending malicious links to the victim’s contact list, requesting money from friends and finally, blackmail from the fraudster to recover the victim’s account in the app. In addition, privacy-related issues, since the fraudster in some cases may have access to the victim’s conversation history when he backs up his conversations in the cloud.
Another problematic issue for victims is the possibility of transfers via Pix (Brazil’s instant payment system) to the fraudster. The agility of this new transfer method has attracted more and more fraudsters because of its fast transfers and the possibility of moving money any day and at any time. So, criminals are able to move and withdraw the amount quickly, before the victim notices and blocks their access. In addition, reversing fraudulent Pix transactions is more difficult than traditional methods such as EFT, with many victims reporting that because they have made the transfer knowingly, the banks end up not returning the money.
Before proceeding with a Pix transfer it’s important to validate the recipient’s full name and SSN snippet.
In case of fraud involving the payment method, the Pix system has an anti-fraud feature that allows you to mark as suspicious all random keys, SSN/EIN and accounts involved in scams. This information is shared between banks in order to deter future scams, so it’s very important that the victim contact the bank as soon as they notice the fraud.
Technical advice
According to a survey carried out by Psafe’s specialized laboratory in Digital Security, in 2020 about 5 million Brazilians were impacted by the scam, since it’s the most used messaging application in the world, WhatsApp becomes attractive to fraudsters due to the great possibilities of attack, simplicity and low cost to execute the coup.
Due to the increasing number of data leakage episodes, it’s important not only to enable two-step verification, but also to evaluate Internet usage and information exposure in an open way, especially on social media.
What we can do to reduce such exposure is to evaluate the apps installed on the smartphone and their terms and conditions of use, as well as their privacy policies in order to identify what kind of information these apps are capturing.
