When it comes to forging documents, it is easy to imagine a scene in which a counterfeit specialist creates almost artistic pieces that cost a lot of money for those who want to use them, but this is a romantic vision; in fact, even though there are a variety of protection mechanisms to avoid document fraud, those that are used daily in Latin America, especially by people interested in registering in digital businesses, do not depend on such sophistication to be produced or to be negotiated. In fact, sophistication is often not necessary to falsify any document.
As the accuracy of the fraud detection mechanisms increases, other ways to circumvent these mechanisms are opened. Tempest’s Threat Intelligence team has been following this struggle for years and was able to see that a blow to fraud overthrows the techniques of many criminals, but there is always that fraudster who dodges that blow, and continues to create new methods to circumvent controls. Over time, these methods are shared among various groups, until the anti-fraud market takes another hit and so the cycle begins again. Between blows and dodges, this is a collection of the most relevant movements we have witnessed in recent years.
Use of Editables
As with many activities, document fraud is a job that, today, depends essentially on digital resources. It is through interaction with images that crime happens. In most cases, there is no need to print any document, as many businesses of interest to the fraudsters are totally digital. Thus, the first movement of documentary fraud was based on making fake documents using files called “editables” or “vectors”.
Vector is a widely used computer graphics file format used in the printing of various materials that depend on image fidelity, regardless of their size. They are much larger files than those based on pixels, for example, because they store a higher volume of information, essential for those who want to make high quality printing.
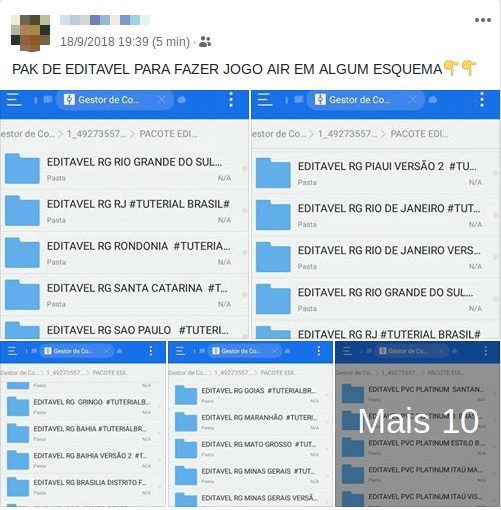
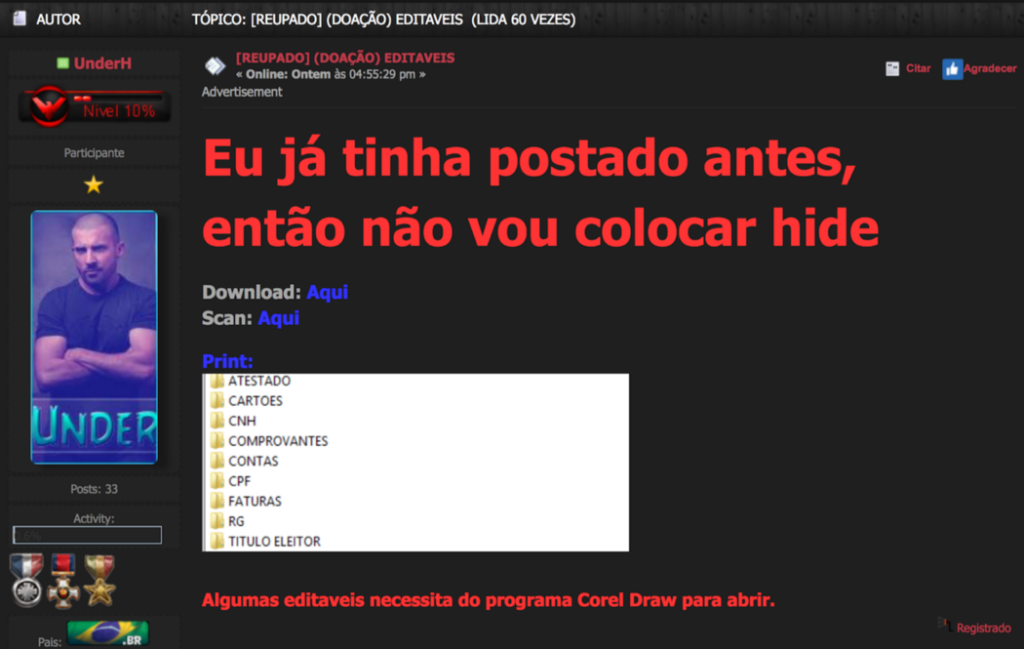
The name “vector” became popular in the context of document fraud; however, the term that is most widely used today is “editable”, which translates into editable templates for CorelDraw and Photoshop. The fraudster can edit these files with the information he wants and insert the photo of the interested person in the document. Very popular among the fraudsters are the editable RG (ID) and CNH (driving licence), but it is also possible to find editable proof of address and the CPF (social security card).
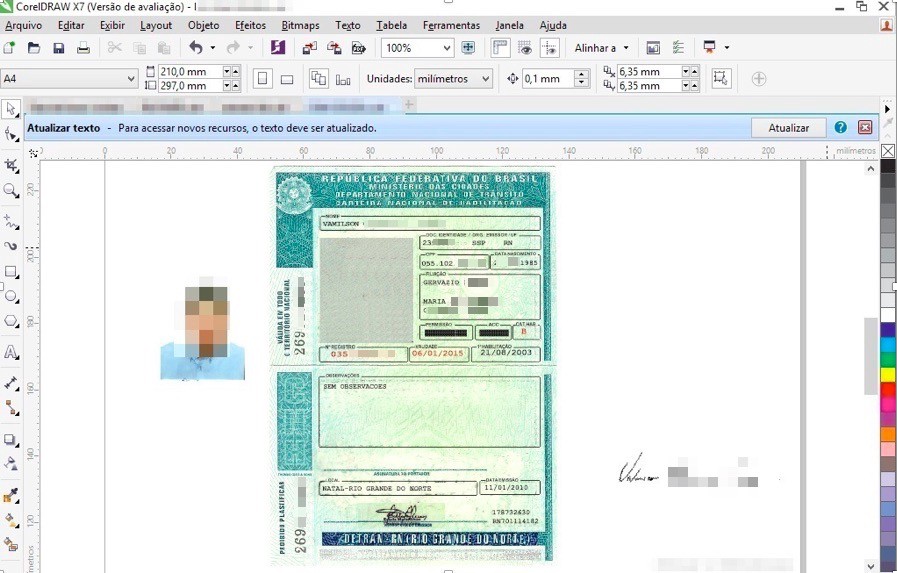
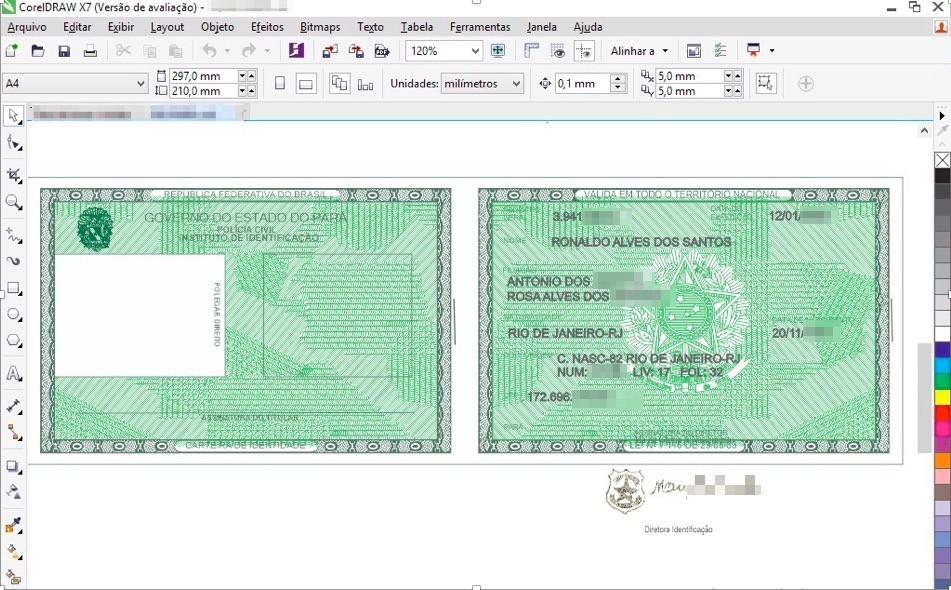
Business Desk
A phenomenon that takes place in several economic activities that migrate to digital environments is that the strong reproduction capacity of digital products — that is, their characteristic of being infinitely copied — tends to take the value of the commodity close to zero. Another factor that also contributes to this is the sharing of the techniques used in each activity, which cease to be a restricted knowledge and become massified.
This also applies to editables, which have become very easy to find, being replicated in various file-sharing services such as Mega and 4Shared; in addition, instructions on how to get them and how to produce them can easily be found on YouTube.
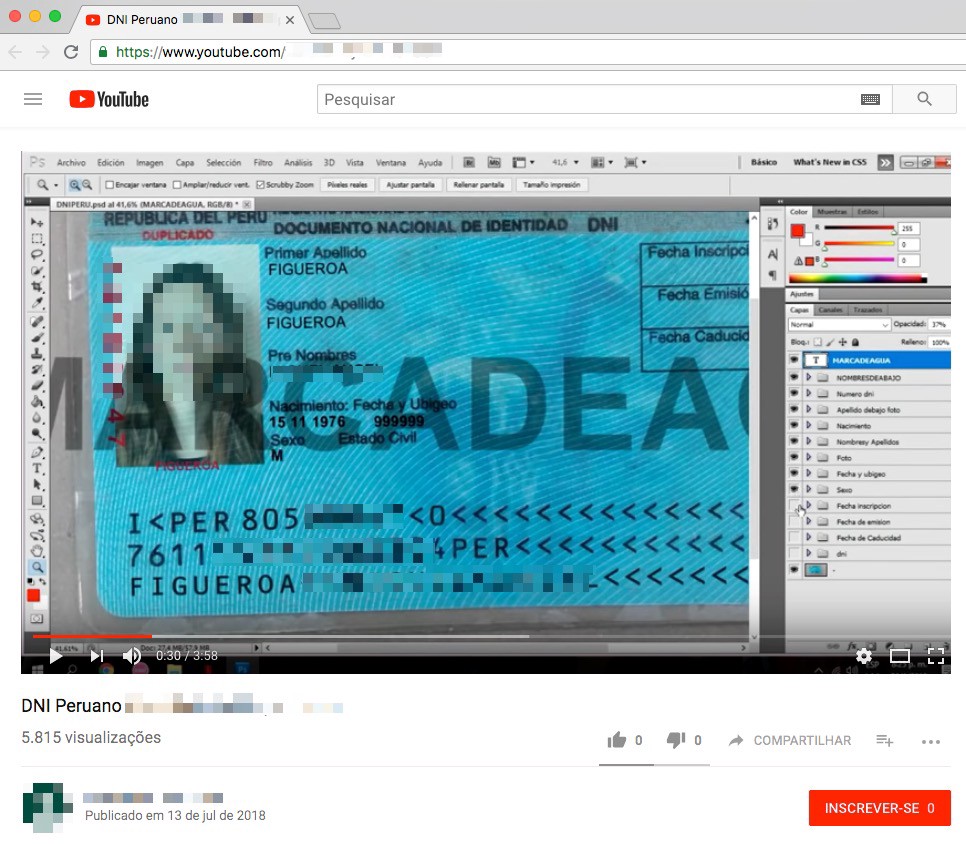
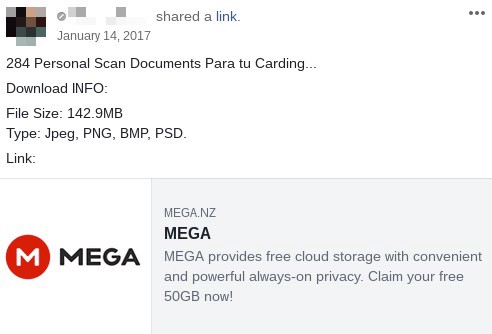
Value is something other than price. The same way that happens with a number of other products whose prices decrease as they become digital, much of the value associated with making such material available, whether for free, at a low price, or as an exchange commodity, is reflected in the reputation that the fraudster can obtain with their community, which may pave the way for their participation in scams with higher financial profits.
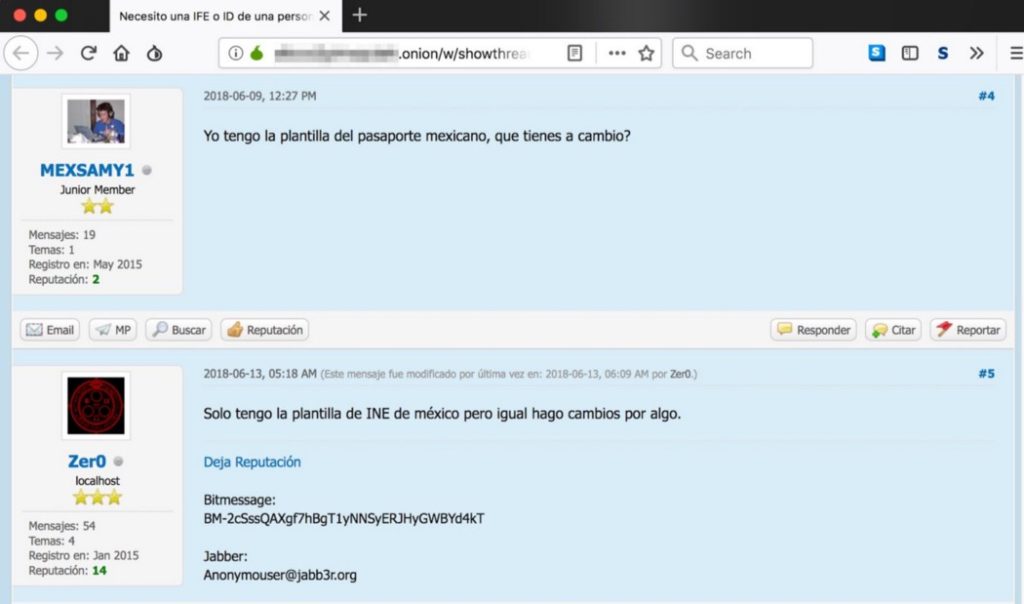
In cases where the files are sold, payments can be made in crypto-coins, through payment services (eg PayPal), through deposit in bank accounts operated by the fraudster and also in forums, in which the moderator operates with a financial intermediary, managing the logistics of payments.
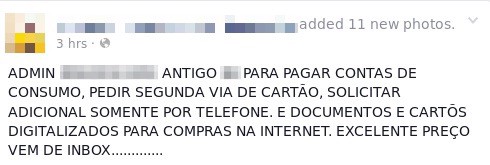
In this sense, it is common to find ads on several digital channels where these files are traded or donated.

Other fraudsters began to automate the generation of some documents. In one of these cases, an address proofing generator was created, in which the user simply fills the screen with any data and prints the document.

These forgeries can still integrate various forms of fraud, such as requesting a copy of a credit card or making online purchases in companies that have not modernized their security mechanisms. However, while the use of editable documents has become popular, anti-fraud technology has evolved, increasing its accuracy in detecting evidence of image tampering. For many criminals, it was necessary to review their practices.
Real people
As chances of using fake documents in scams effectively got reduced, criminals began to look for alternatives in which to obtain copies of true documents.
This is possible by the co-opting of employees, by using privileged access credentials in corporate systems, or by means of attacking companies that deal with document management and by constantly negotiating leaked company data
These scenarios can be combined. For example, imaging may include the combination of granting privileged access to a system by a co-opted employee through which it is possible to leak its entire base and then trade it on different fraudster channels. However, the modalities will be discussed in isolation here for analysis purposes only.
Employee cooptation can happen in companies of different segments whose activity involves the continuous interaction with documents. Last year we noticed a rise in the volume of offers from these types of files shortly after the press denounced a scheme in which attendants of a Brazilian retailer were selling copies of documents.
Privileged access to systems is also very common. There is a market for temporary access to systems of companies of all sizes. Everything that is extracted from these repositories can generate some value in frauds.

Privileged accesses can be sold or leaked, but many of these connections are also obtained in direct attacks against corporate systems, in which vulnerabilities with varying degrees of criticality and ease of exploitation can pave the way for obtaining documents.
Among the favorite targets of the attackers are car rental companies, insurance companies, financial institutions, travel agencies and any other companies whose business depends on the accumulation of these images. However, at the top of the list are companies whose role is to manage documents.
Over time, many companies have incorporated a new component into their identity validation process, asking the applicant to send a selfie in which he or her is holding an identification document. Again, this helped to stop many frauds; however, just as in other cases, alternatives were created to circumvent this control.
Selfies
One of the paths fraudsters have taken in dealing with the selfie requirement was to create editable documents and pay for “stooges” to appear in the photos holding the fake document. However, while this is a widely used tactic, it can be filtered by anti-fraud services in many companies.
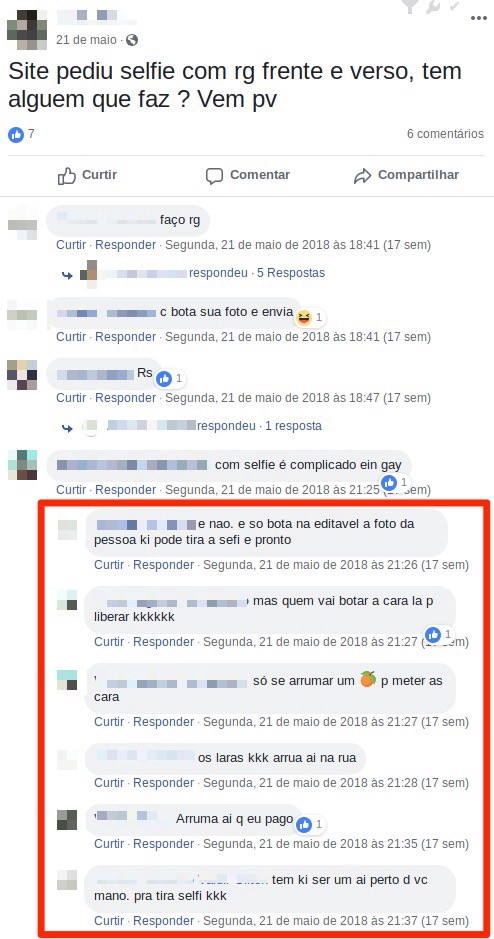

Attacks against repositories and privileged accesses in systems mentioned above also serve as an alternative to taking pictures of real individuals and their documents, however, fraudsters have opened another front to get these images directly from consumers, using phishing attacks.
Harvesting
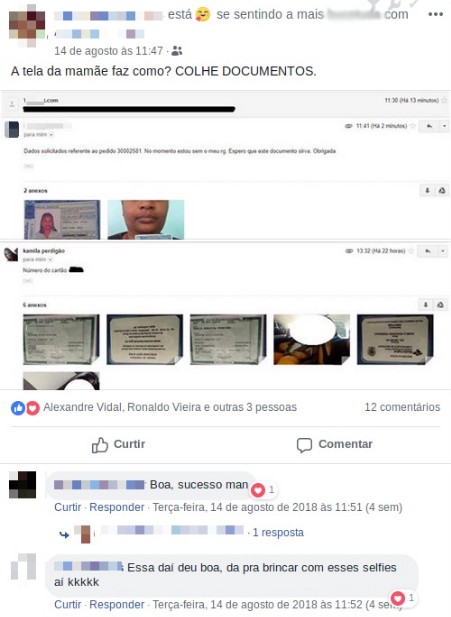
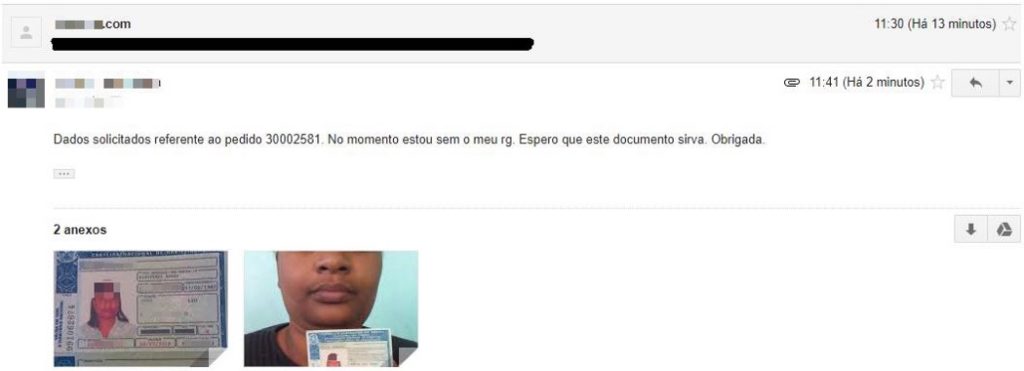
Recently a new way to persuade consumers to deliver images of their documents and their selfies has emerged. Fraudsters use fake websites mimicking large online stores, offering products priced well below the market. These “offers” are advertised on Facebook sponsored ads and can attract a lot of people.
The victim then complies with all steps of a traditional e-commerce purchase process, submitting registration and payment data. After completing the process, the victim receives an email from the fraudster asking to send photos of the document and a selfie with it for security verification.

Fighting Fraud
This document is a collection of many techniques that have emerged over the years. None of them fell into disuse, but many were remodeled, combined with others or modernized. Fighting fraud is an activity that involves the implementation of controls, but also requires continuous monitoring in various external channels to identify changes in the course of criminal activity. Therefore, it is recommended that companies evaluate the contracting of intelligence services.
Reviewing access controls and monitoring systems is also very important, especially in companies that manage documents in order to identify suspicious access and protect personal data.
As for the general public, it is very important to be wary of offers with prices that are much lower than the market; it is worth comparing those offers with prices in other places, as well as carefully checking the address of the website where you are making the purchase. It can also be considered as a security measure, while sending images to legitimate sites, the inclusion of a text in all the images saying that the image was sent to the requesting company, for registry reasons.
